Privacy is not guaranteed by any universal law, and several current or developing technologies are real threats to our privacy. In this article, we look at 5 technologies that are poised to strip our privacy and what, if anything, you can do to defend against them.
The Technology: Jetson Biometric Heart Rate ID System
How would you feel about a system that can automatically identify people from hundreds of meters away by reading their heart rate? Meet Jetson, a prototype system built due to keen interest from US Special Forces. Currently capable of identifying someone from 200 meters away using an infrared laser, the developers expect to greatly increase the range over time.
While it is a surprise to most people (including us), everyone’s heart rate varies, resulting in a unique cardiac signature for every person. Even if everyone does have a unique cardiac signature, how can you measure it with a laser from hundreds of meters away?
According to an article from MIT Technology Review:
At the moment, Jetson only works on stationary targets, but surely the developers will be attacking that limitation soon. Wenyao Xu of the State University of New York at Buffalo, who independently developed a shorter-range system based on radar, says that cardiac signatures have the potential to be more accurate than facial recognition systems and could achieve 98% accuracy.
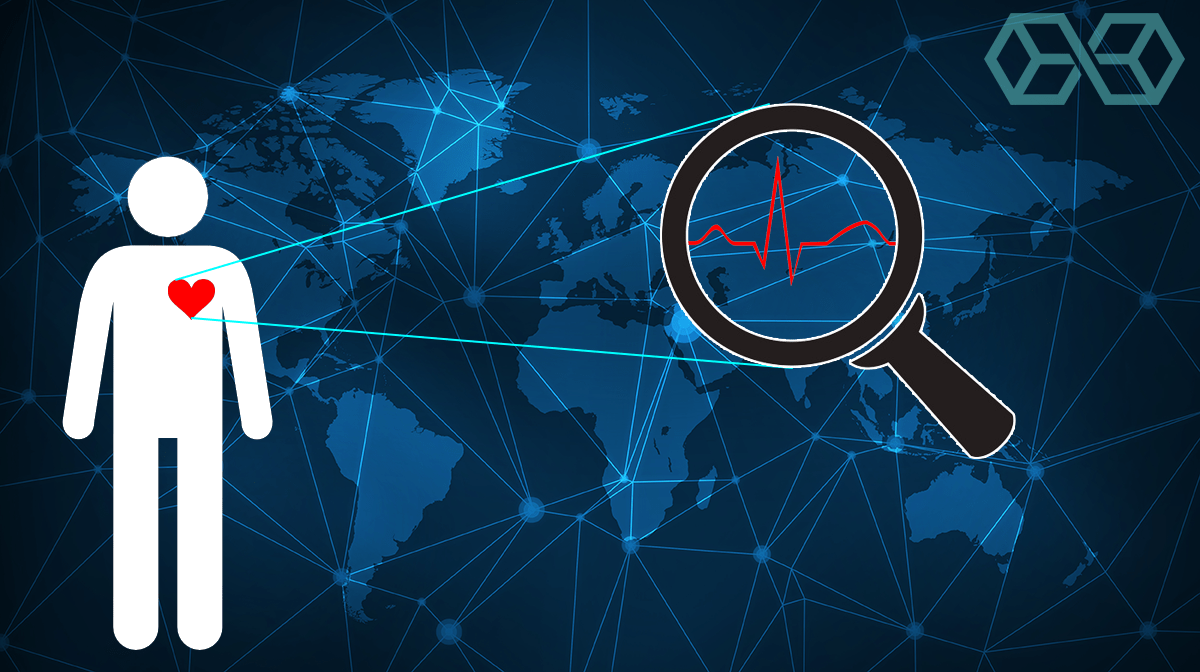
The privacy implications of this new technology are profound. Right now it can be used retroactively, say by recording signatures of masked people involved in a protest, and later using the recorded signatures to make a positive ID among suspects.
Taking things to their logical conclusion, how long will it be before governments start routinely recording cardiac signatures of their populations? Being able to ID people from a long distance automatically would surely make spying on your own people easier.
The Defense Against Jetson
As far as we can tell, there are only a few things you can do to protect your privacy against government agents armed with Jetson:
- Wear Heavy Clothing. The laser used in Jetson measures the movements on the surface of your body that are caused by your heart. Heavy enough (whatever that might mean) clothing should prevent the system from getting a usable reading.
- Keep Moving. It reportedly takes around 30 seconds to get a usable cardiac signature. By staying on the move, you may be able to prevent the system from gathering enough data to create a signature.
The Technology: Advanced Facial Recognition Systems
Facial recognition systems are already used by repressive governments like China to monitor their populations (as well as by many Western countries such as England). But these systems are still evolving and are being connected to AI systems that will make them far greater threats to our privacy.
For example, the bodycams that in the past were used by police departments to make sure officers behave responsibly are now being turned into civil surveillance devices. Companies are working to tie police bodycams to AI-driven facial recognition systems.
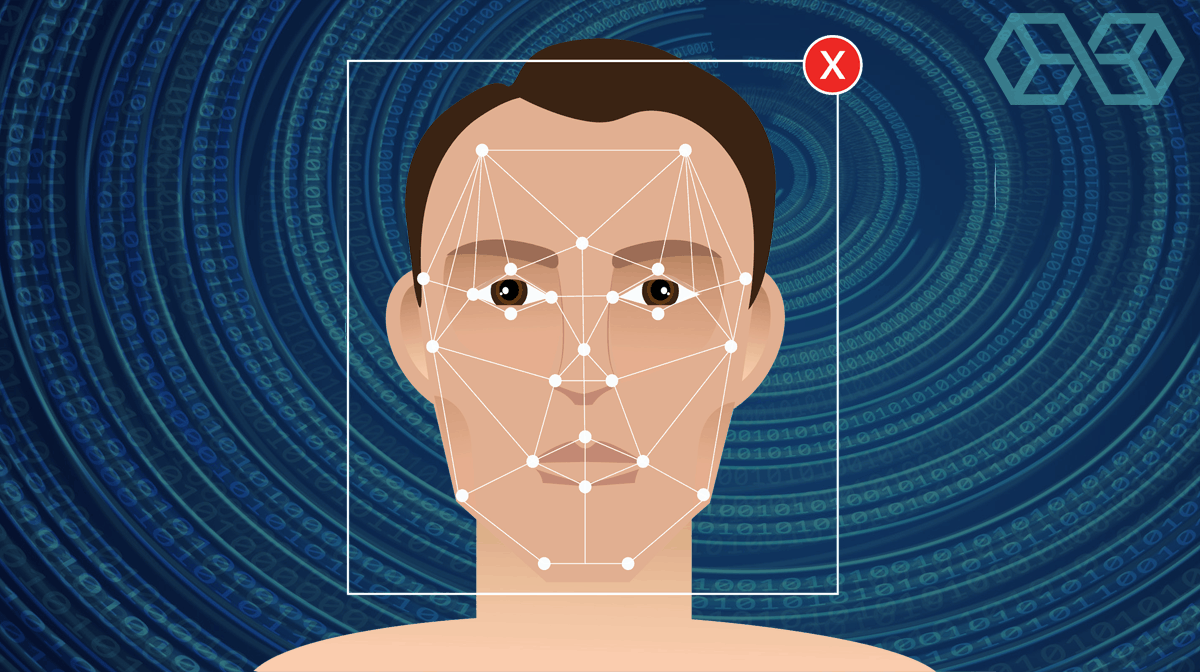
Theoretically, this would allow police departments to identify every person their officers encounter in real-time. While this would be very helpful in situations where an officer confronts a violent criminal, it would also enable a database of the locations of law-abiding citizens. Another scary possibility is that the systems could signal the police to confront citizens solely based on the facial ID.
An officer patrolling an area probably encounters hundreds, if not thousands of people a day. Even if the facial recognition system could be optimized for 99% accuracy (far more than they can now achieve), it would lead to huge numbers of misidentifications across an entire police force.
The Defense Against Advanced Facial Recognition Systems
Because these systems need a clear view of your face, you might be able to defend against them by:
- Obscuring Your Face. When going into public areas, particularly those where there is likely to be surveillance or a large police presence, you could obscure your face. Wearing a hat can make it harder for overhead cameras to see your face. Dark glasses or facial hair could confuse these systems when your face is visible to cameras.
- Avoiding Cameras. Preventing cameras from seeing your face would, of course, prevent a facial recognition system from working. However, apparent steps like wearing a mask or otherwise hiding your face have their own risks. There have been numerous cases in the UK where the police questioned or fined people who did nothing more suspicious than pull up the collar of their jacket or turn their face away when passing police officers conducting facial recognition tests.
- Support Government Restrictions on its Use. The apparent risks to privacy inherent in these systems have triggered some action to limit their uses. One example is California Assembly Bill AB-1215, which would, “…prohibit a law enforcement agency or law enforcement official from installing, activating, or using any biometric surveillance system in connection with an officer camera or data collected by an officer camera.” This bill has already been brought into law.
The Technology: Homeland Advanced Recognition Technology (HART)
Imagine a system that combines facial recognition, DNA test results, police reports, voiceprints, patterns of scars and tattoos, information from airlines and other travel-related sources, and “non-obvious relationship patterns,” (whatever the hell that means) into a giant collection of databases. Now imagine such a system being used by a wide range of government agencies for all sorts of purposes, without any oversight or control by elected political authorities.
You’ve just imagined the Homeland Advanced Recognition System (HART). The US Department of Homeland Security (DHS) is rolling out this system now, despite opposition by many public interest groups and members of Congress.

HART relies heavily upon facial recognition systems that scan both visitors and US citizens. As far as we have been able to discover, DHS has never been authorized by Congress to scan the faces of US citizens. Regardless of whether such scanning has been approved or not, it is being used. However, according to a 2017 report by the Center on Privacy & Technology at Georgetown Law:
DHS plans call for HART to be deployed against every international flight in the United States by the end of 2021.
The Defense Against HART
There appears to be only one thing a person can do to avoid having personal information gathered into HART:
- Avoid International Air Travel Into, Out of, or Through US Territory. DHS has made it clear that they intend to track everyone who travels internationally, US citizens and foreign nationals alike. As they put it in the Privacy Impact Assessment Update for the Traveler Verification Service (TVS): Partner Process DHS/CBP/PIA-030(c) June 12, 2017:
There are Some Rays of Hope
While there is currently little you can do to protect yourself against the privacy-violating technologies we have been looking at, there are areas where you can take effective action. Let’s look at them now.
The Technology: Web Trackers
Once upon a time, the ads that appeared on the web pages you visited were just ads. They appeared because they were relevant to the content of the page. Aside from taking up space, they were harmless and provided a way for a website to make money while offering their content for free.

Today the ads that you see are more likely to be related to things you viewed recently elsewhere on the Internet. And they are likely to carry web trackers that let advertisers spy on your browsing history.
What happens to the information they gather? They may use it themselves to better target their ads. Or they may sell it to other advertisers. In either case, the result is that information about what you do online is gathered into giant databases without your consent.
You might think that the information gathered by the ads must be anonymous, but you would be wrong. Given enough data, there are techniques that companies can use to identify you with a high degree of accuracy, even if you never directly reveal personal information to them.
The Defense Against Web Trackers
There are two related defenses against web trackers:
- Install a Pro-Privacy Browser Extension. In the case of web trackers, we do have effective protection. There are several pro-privacy browser extensions you can install that kill ads containing web trackers. They aren’t perfect–information about what you do online is worth a lot of money–so there is an ongoing war between pro-privacy tools and web tracker developers. In addition, these browser extensions can break some sites, requiring you to make some manual adjustments. Even so, the right browser extensions provide a strong defense against web trackers.
- Use a Browser with Built-In Blocking. A couple of web browsers are available that have ad-blocking / web tracker defense built-in. One is Opera; the other is Brave. Just like browser extensions, the blocking features of these secure browsers do break some websites and require you to make minor adjustments from time to time. But both are free to download and use, so well worth experimenting with.
The Technology: Established Social Media Giants
The world of Social media is dominated by a handful of organizations: Facebook, Youtube, Twitter, and a few others have a stranglehold on the ways we interact online. They all seem to have a strong political agenda, along with the will to use their power to impose that agenda on the world. The result has been purges of users with “unacceptable” opinions or political positions, along with more insidious tricks like shadow banning of those who don’t conform.

Even if they had no apparent political biases, numerous scandals over the last few years have shown that these companies do not respect user privacy and do a terrible job safeguarding the information they have about us.
Until recently, network effects (the more users they have, the more valuable and popular they become) have made their positions unassailable.
The Defense Against Current Social Media Systems
Alternatives to the established social media giants have begun to appear. Free-speech sites like Minds and Gab have been in the fight for years, but are vulnerable because they are centralized systems like the giants they want to replace.
Now a new wave of federated or decentralized services is appearing. For example, while we were preparing this article, Gab, with nearly one million users already, announced a complete redesign of their service. According to the announcement:
In other words, Gab is moving to a federated model. Their goal is to make Gab censor-proof, resilient, and anti-fragile. While federated systems like Gab are still dwarfed by the current giants, their designs will allow them to grow rapidly and provide platforms for people around the world who are not well served by or explicitly banned from, the current system.
The Future
We are now starting to have some nice pro privacy alternatives like browsers, cryptocurrencies, VPN technology, decentralized social networks and so on. But are they enough to stop the onslaught on personal privacy from technological innovation? We only think they can tide the stem, but not stop it.
If you are a very privacy conscious person you have alternatives, but you will need to jump through some hoops to do so. Switch to linux, use a VPN service (like NordVPN or ExpressVPN), use a secure browser and only use bitcoin to make payments.
For the average person, convenience is key and technology is making everyday life way more convenient. We don’t see that trend changing anything soon, if not ever.


![A Beginner’s Guide to Monero – What Is XMR? [Updated 2023]](https://cd.blokt.com/wp-content/uploads/2019/04/Beginners-guide-to-Monero-2-218x150.png)

![Best 5 Bitcoin Sports Betting Sites [2023] (Analyzed & Approved) Best Bitcoin Betting Sites](https://cd.blokt.com/wp-content/uploads/2020/05/best-bitcoin-betting-sites-218x150.png)

