The dictionary definition of a ledger is a “book or other collection or financial accounts.” Before the advent of electronic storage, government and financial institutions kept their records stored in paper ledgers.
While the thought of old-fashioned paper books filled with hand-written records is somewhat charming, the data stored in these paper ledgers were extremely vulnerable to… well, all of the things that paper is susceptible to–fire damage, water damage, even just getting lost.
When it became possible to store data digitally, it also became much easier to replicate data. What would have had to be hand-copied in the past could now be copied with the push of a button, and if a server was destroyed, the likelihood of an available backup copy was much increased.
However, even with backup copies, digital data that is stored in any sort of centralized fashion is still vulnerable to many factors. The backup copies must be kept up to date, as new data could be lost if they are not.
Additionally, the central server or its backup copies could be vulnerable to hacking. Any hacker that gained access to the data through the original server or any of its copies would have access to all of the data stored there. For example, a hacker that gained access to a bank’s private server could have access to the personal information associated with thousands of accounts.
Today, most of our personal information is stored on centralized servers, or–in some cases–on paper. Our bank accounts, marriage certificates, and mortgage contracts exist in forms and locations that leave them vulnerable to a variety of factors.
The Rise of Decentralized Ledgers
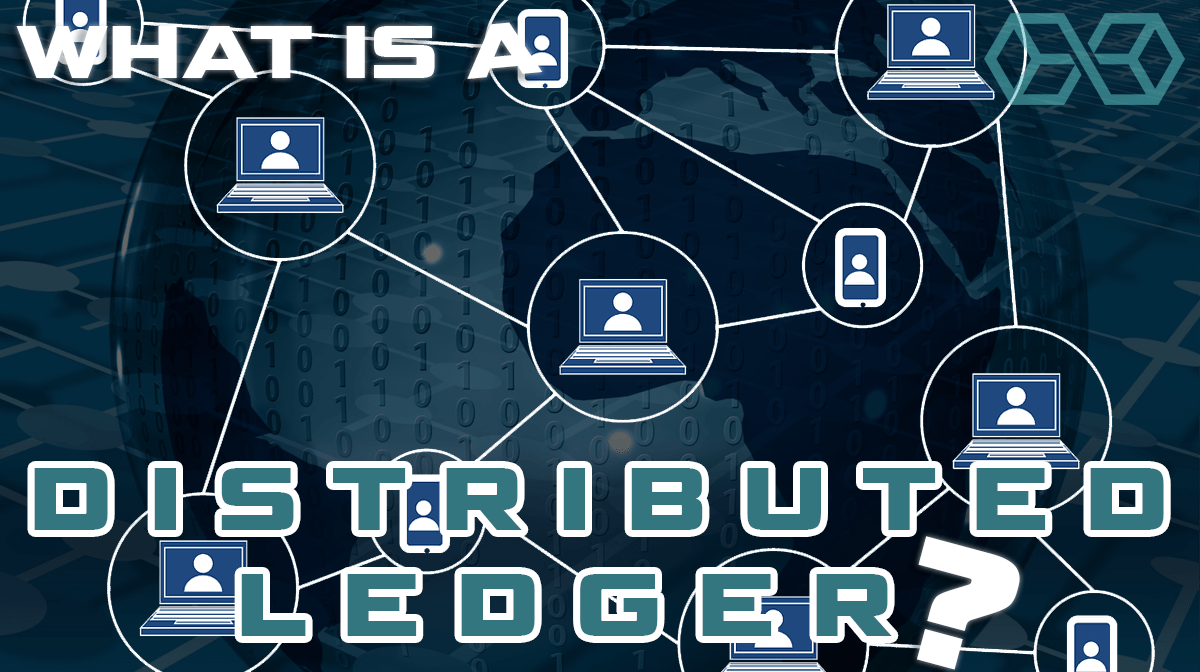
In recent years, a decentralized, cryptographically-based method of transacting with and storing data has been formed. This technology called a ‘distributed ledger,’ often shortened to ‘DLT,‘ stores data in a way that is virtually impervious to hacking or indeed anything else that could compromise its safety or permanence.

Blockchain is a form of distributed ledger that is the basis on which cryptocurrencies are formed, but blockchain applications extend far beyond just cryptos.
A distributed ledger is not stored in any centralized location. Instead, it runs in hundreds or thousands of locations across a network of computers. Because of this, it is not vulnerable to hacking or the other kinds of potential problems that endanger the data stored on a centralized server. The decentralized nature of a blockchain makes it virtually impervious to hacking, tampering, or any other sort of destruction of data.
The computers that uphold a distributed ledger network are called nodes. Nodes also perform the tasks necessary to validate transactions on the network. The process by which these tasks are performed is called mining. In exchange for their work as miners, the nodes are rewarded with crypto tokens.
For a distributed ledger to be hacked or otherwise damaged, more than half of the nodes would have to be somehow compromised. Because blockchain-based networks often have hundreds or even thousands of nodes, there is little chance that this could ever happen.
While the users’ identities are protected using a variety of different methods, the ledger is public. This ensures that transactions that happen on the network are valid and are not repeated, simply because everyone can see what is happening.
Why are Distributed Ledgers Called ‘Trustless’?
Distributed ledger networks are trustless. When readers first come across this term, it may seem negative – isn’t a lack of trust a bad thing?
However, in this scenario, trustless means that users of the system do not have to place their trust in any centralized entity (like a credit card company or bank) to ensure that their transactions are valid. With distributed ledger technology, it is impossible to fake a transaction.
While distributed ledger technology and cryptocurrency are still in their very early stages, many new use cases for these technologies are being conceptualized and implemented every day, including:
- Creating digital identity through the use of public and private crypto addresses
- Storing records, including the storage of legal documents (ie, marriage certificates and mortgage contracts); data can be encrypted and/or hashed
- Acting as a settlement layer for the development of decentralized applications
- Serving as a platform for the creation and execution of smart contracts
While there are new kinds of cryptocurrencies that are based on new kinds of distributed ledger technology (i.e., IOTA’s “Tangle”), most cryptocurrencies are based on blockchain technology.
How Does Blockchain Work?
If you’ve spent more than a few seconds involved in the crypto community, you’ve probably heard or read the word blockchain before now. However, what really is a blockchain?
In essence, it’s quite simple: a blockchain is a kind of distributed ledger that holds the data of all of the transactions that happen in a peer-to-peer network. In other words, it’s a public record of all of the transactions that occur in a decentralized network; no third-party entity owns or operates the network.
Let’s explore this a bit further with a comparison to a credit card company. Johnny buys a $5 coffee from Ashley using his credit card. The credit card machine sends a signal to the company that $5 should be removed from Johnny’s account and placed into Ashley’s account. All of the data involved in this transaction is stored on a centralized server that is privately owned and operated by the credit card company.
The credit card company needs the necessary hardware and software to complete the transaction and to keep a record of it. It needs employees to maintain its private system, buildings to house the operation, a marketing team, a legal team–you get the picture. The credit card company would also like to make a profit. Accordingly, the credit card company charges its users for the use of its card.
Because the credit card company stores all of its transactional data (and its users’ personal data) on a centralized server, all it would take is a single successful hacking attack to compromise everything stored on the server. Although it is less likely, the servers could also be compromised by physical damage (i.e., fire or water).
Now, let’s re-imagine this transaction as if it had happened on a decentralized, blockchain-based network. The transaction would not be validated and stored by a central, third-party company; instead, it would be validated by other computers on the network and stored in a group of data called a block. When a block is “full,” it is added to the blocks that came before it in a linear fashion, forming a “chain” of data. Thus, the name: “blockchain.”
Cryptocurrency is quickly becoming very popular, and there are so many buzzwords surrounding the cryptocurrency industry that it can sort out the ‘media speak’ from the real substance.
Although blockchains are a type of distributed ledger, distributed ledgers are not always blockchains. Distributed ledgers might be internal within a business, without being a public ledger, in which case it doesn’t adhere perfectly to the definition of a ‘blockchain.’

For more easy-to-understand guides and information that will keep you on the cutting edge of the world of cryptocurrency and distributed ledger technology, head over to our guides section to learn more.
What are your thoughts on the future of distributed ledger technology? We would love to hear what you have to say–leave a comment below.
References
- IOTA Whitepaper
- 51% Attack Explained
- Difference Between Centralization and Decentralization

![A Beginner’s Guide to Monero – What Is XMR? [Updated 2023]](https://cd.blokt.com/wp-content/uploads/2019/04/Beginners-guide-to-Monero-2-218x150.png)

![Best 5 Bitcoin Sports Betting Sites [2023] (Analyzed & Approved) Best Bitcoin Betting Sites](https://cd.blokt.com/wp-content/uploads/2020/05/best-bitcoin-betting-sites-218x150.png)

