If you want to protect your privacy online, you need to know about and start using Tor. In this article, we will talk about what Tor is, along with who uses it and why.
From there, we’ll get into exactly how Tor works, how it provides anonymity, and the limitations of the service.

We’ll finish up by walking through downloading, installing, and starting to use Tor on your own computer.
What is Tor?
Tor began its life in the 1990s when researchers at the US Naval Research Laboratory developed “onion routing.” Onion routing makes it possible to pass messages through a network anonymously. It uses multiple layers of encryption that get peeled off one by one (like peeling an onion) as the message passes through multiple nodes in the network.

In 2004, the Navy released the second generation of Tor. In 2006, researchers involved in Tor incorporated the Tor Project and took responsibility for maintaining Tor.
Tor stands for the onion router. It is a network of thousands of computers around the world that implements onion routing. Originally designed to protect US Intelligence Agency communications online, it now serves millions of users, military, government, and civilian, in every country on Earth.
How does Tor protect your privacy?
We were going to try to explain how Tor protects your privacy, but why not let the Tor team do it themselves?
Who uses Tor?
People from around the world who want to / need to protect their privacy by using the Internet anonymously use Tor. Here are some of the types of users we’re talking about:
- Citizens and journalists in repressive countries who need to get information to the world.
- News services like the New York Times and The Guardian host who use the Secure Drop program to communicate with whistleblowers.
- Law enforcement uses it for everything from anonymous tip lines to surveillance of websites and sting operations.
- Human rights activists from individuals to groups like Human Rights Watch and Global Voices.
- Businesses that need private communications or anonymous feedback from staff.
- Government agencies and militaries that need secure communications.
- Millions of regular people who want or need their activities online to remain private. They use it to get around government censors to research sensitive topics, and to avoid monitoring by their ISP, nosy websites, and government busybodies.
To get an idea of how many people use Tor, as well as all sorts of other statistics, visit Tor Metrics.
Is it legal to use Tor?
As far as we can determine, it is legal to use Tor anywhere in the world. That might be surprising but look at all the different types of users. Governments and law enforcement agencies around the world rely on Tor, as do all sorts of civilian groups.
Is it safe to use Tor?
Whether Tor is safe or not depends on what you mean by safe.
Is the Tor Browser safe to use (free of spyware and so on)? Yes, if you download it from the official Tor Project page.
Is the Tor network safe to use? Yes, if you use Tor to browse regular websites.

Is every place you can visit with Tor safe and legal? Hell no! Tor gives you access to sites on the Internet that you can’t reach with Google Chrome or other regular web browsers. But so what? You can use a regular web browser to go to places on the public Internet that aren’t safe or legal either.
As with most other things in life, whether Tor is safe or not depends on you using it safely.
Using Tor Might Attract Unwanted Attention
While you may use Tor safely and legally, the fact that you are using it may attract unwanted attention. Law enforcement and spy agencies around the world are likely interested in anyone using Tor or any technology that makes it harder for them to spy on you.
As Edward Snowden showed us years ago, the US government and numerous others seem intent on spying on 100% of everything that everyone on Earth does online anyway. But it is possible that some human or AI (Artificial Intelligence) analyst might pay more attention to the info they gather on you if you use Tor. You’ll need to decide if doing things anonymously is worth the possibility of increased attention by these groups.
Can Tor be hacked?
It is theoretically possible to hack Tor. The network was hacked in 2014, apparently by the FBI. There are also more recent stories of the computers of Tor users being hacked to get information for criminal investigations.
In addition, a sufficiently powerful entity (a global adversary) could theoretically monitor all of the entry and exit points of the Tor network. Using statistical analysis, they could likely de-anonymize users of the network.

So yes, Tor can be hacked. But again, so what? Nothing in this world is 100% foolproof. If you want to protect your privacy online, using Tor can help. If you want to do something that will set the NSA, KGB, NCCU, or other powerful security agencies on your tail, there may be nowhere you can hide.
How does Tor work?
Understanding the basics of how Tor works isn’t hard. Understanding it in depth is a lot tougher. We’ll go through the basics first. If all you want to know is the basics, great. You can skip ahead once you are done with this section.
If you already feel a bit overwhelmed by Tor, but you still want some basic privacy, then we recommend a good VPN service. Nordvpn or Expressvpn are the top two privacy-focused VPN services according to our best vpn services guide.
We’ll also cover the details in more depth for anyone who is interested.
How Tor Works: The Basics
When you visit a website normally (without using Tor), your computer makes a direct connection to the computer where the website is located. The problem with this is that when you do it this way, the website can see all sorts of information about you. It can see your computer’s IP address, the operating system you are using, the web browser you are using, and more. That information can be used for tracking what you do online and possibly identifying you.
When you use Tor to visit a website, things get more complicated. The connection between your computer and the website passes through three random computers in the Tor network. Each of those computers only knows which computer gave it data and which it gives data to. No computer in the network knows the entire path. Meanwhile, the only thing the website can see is that it is connected to the final Tor computer in the path.
As a result, there is no way to identify you based on the connection between your computer and the website. This makes your connection anonymous.
How Tor Works: The Details
When you visit a website without using Tor, your computer establishes a direct connection with the computer hosting the website. Data packets pass back and forth between the two, enabling you to view and interact with the website.
Each data packet consists of the data itself (the payload) and a header with additional information, including data about your web browser, and the IP address of the source and the destination. At a minimum, a website (or anyone spying on your connection with the website) can use the IP address to figure out approximately where you are located.
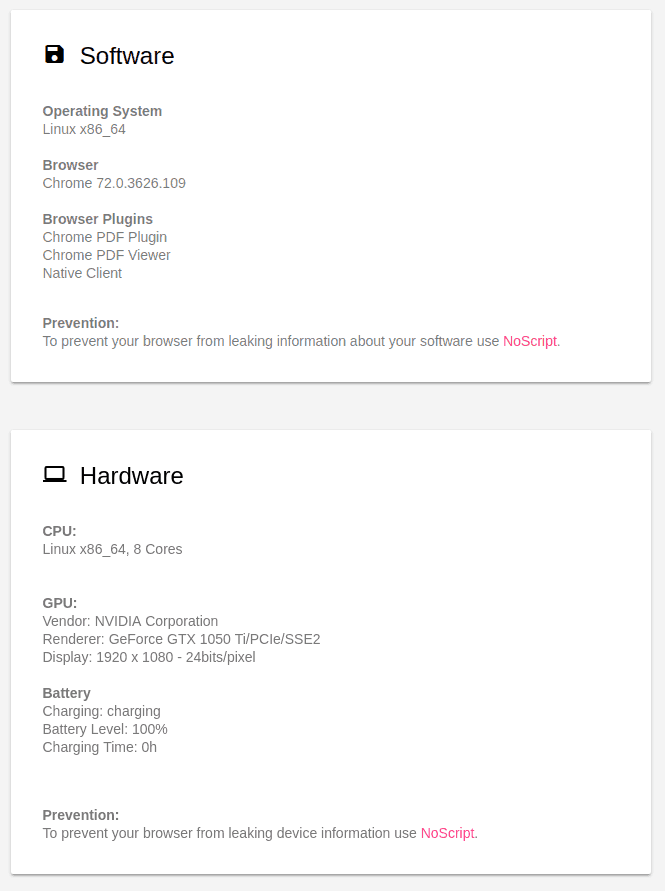
Beyond that, a web browser will automatically share all sorts of information with any website it connects to. This includes things like who your Internet Service Provider is, what Operating System your computer uses, your video display mode, even the power level of your laptop battery. The figure above shows just some of the data my computer gave up when I connected it to ‘What every Browser knows about you,’ a site designed to show you what your computer is telling the world without your knowledge.
Tor prevents this from happening.

When you connect to the Internet using the Tor Browser, the browser connects to a random entry point (Guard Relay) on the Tor network. The browser negotiates an encrypted connection with the Guard Relay. Data sent along this connection is encrypted using these keys so only your browser and the Guard Relay can decrypt them.
Your browser then negotiates another connection, this one from the Guard Relay to another computer in the Tor network called a Middle Relay. For this connection, it creates another set of keys that are used by the Guard Relay and Middle Relay.
Finally, your browser negotiates a third connection. This is between the Middle Relay and an Exit Relay. Again, it negotiates a set of keys that will be used to encrypt and decrypt data passing along the connection between the Middle Relay and the Exit relay.
Data passing from your browser to the Internet gets encrypted three times.
- First, it gets encrypted using the keys for the connection between the Exit Relay and the Middle Relay.
- Second, it gets encrypted with the keys for the connection between the Middle Relay and the Guard Relay.
- Third, it gets encrypted with the keys for the connection between the Guard Relay and your browser.
Your browser passes the triply-encoded data to the Guard Relay. The Guard Relay strips off the outermost layer of encryption. Two layers of encryption still protect the data itself. All the Guard Relay knows is where the data came from, and what Middle Relay to send it to.
The Guard Relay passes the now doubly-encoded data to the Middle Relay. The Middle Relay strips off the next layer of encryption. A layer of encryption still protects the data itself. All the Middle Relay knows is that the data came from the Guard Relay, and what Exit Relay to send it to.
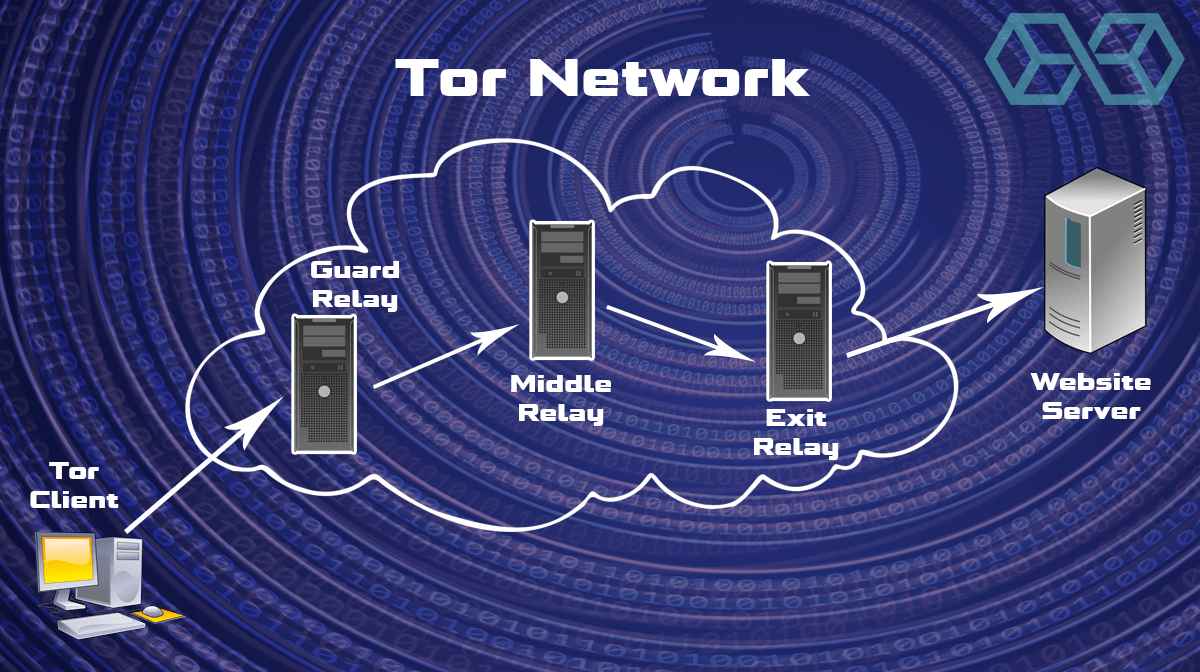
The Middle Relay passes the singly-encoded data to the Exit Relay. The Exit Relay strips off the final layer of encryption. The data itself is now unprotected. The Exit Relay can see the original data, but it doesn’t know that this data originated at your browser. All it knows is that the data came from the Middle Relay, and what website to send it to.
The website receives the data from the Exit Relay. As far as the website can tell, the data originated at the relay. It has no way to tell that the data originated at your browser.
Because no node in the path knows the entire path between your computer and the website, the transport of data between the two is anonymous.
What are Onion Services?
Onion Services are online services that you can reach through Tor but are not accessible using a normal web browser or the standard Domain Name System (DNS).
When you use the Internet normally, you can only see the web pages that are indexed by search engines. This is called the Surface Web. But there is another part of the Internet that you can’t see. This is called the Deep Web.
The Deep Web is the part of the Internet that is not indexed by search engines. It includes things like corporate databases, government resources, medical records, and so on. Anything that is on the Internet but that doesn’t show up in search engines. Researchers estimate that more than 90% of all the information on the Internet is within the Deep Web.

If you know the address and have the right permissions, you can interact with most Deep Web sites using the same stuff you use on the Surface Web.
Onion Services occupy a part of the Deep Web known as the Dark Web. You need special browsers and/or protocols to interact with Dark Web sites. The Tor Browser handles all this so you can interact with Onion Services.
All Onion Services have a 16 character name derived from the service’s public key and end with .onion. For example, if you entered this http://rougmnvswfsmd4dq.onion/ into a standard web browser, it would give you an error something like this:
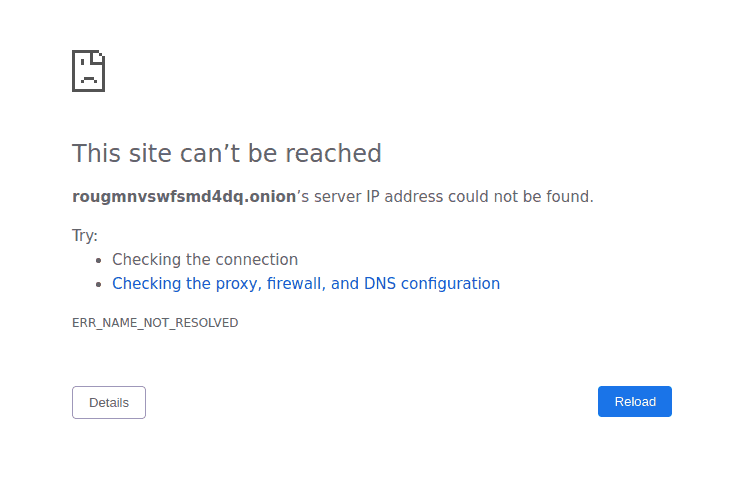
Enter the same thing into the Tor Browser, and it would take you to the Tor Metrics Onion Service, which happens to look like this:
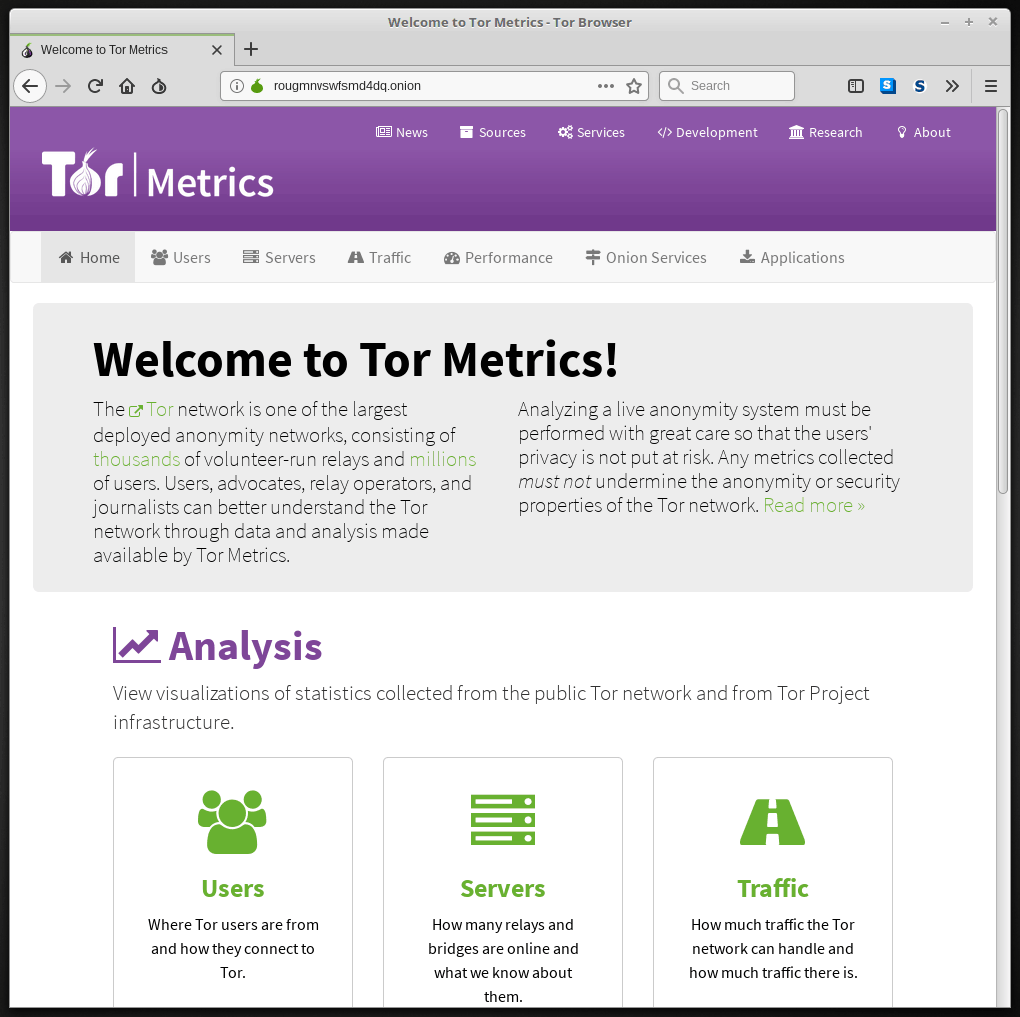
With names like these and no way to find them through regular search engines, it is clear that you aren’t going to just stumble across Onion Services. That makes sense since Onion Services are designed to protect the anonymity of both the person providing the service and the person using it.
But how do you find them?
One way is to use special indexes. Indexes are lists of Onion Services. They are not search engines that are machine-generated and maintained. Each Index is compiled and maintained by hand. Here is an example of an index:
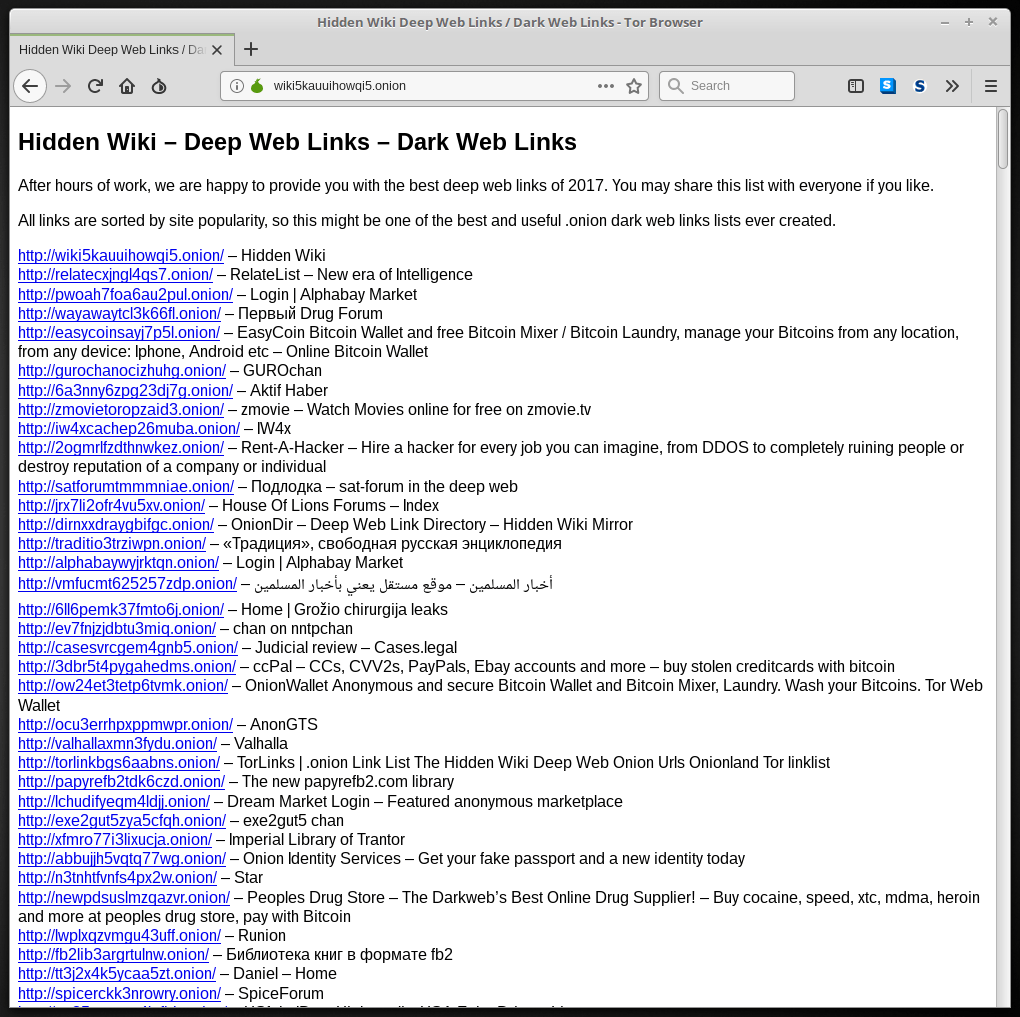
Indexes only include a tiny fraction of the Onion Services that exist. So how else do you find Onion Services?
Some of the popular search engines in the Surface Web have Onion Services as well. Here’s one privacy-friendly search engine with its own Onion Service, DuckDuckGo:

This looks promising, but when you do a search, the results aren’t Onion Services. They are just results from the Surface Web.
There are some Onion Service search engines out there. But the ones we looked at while preparing this article didn’t seem to give good results and offered lots of ads for the kinds of stuff that give the Dark Web a bad name. We wouldn’t recommend using them.
Besides hand-made indexes and sketchy search engines, your options are limited. Word of mouth is one way. Following links from one Onion Service to the next is another. In other words, it isn’t easy to find Onion Services that aren’t listed in an index.
Sometimes Onion Services Show Up in Search Engines
Despite what we just told you, Onion Services do sometimes show up in searches on regular search engines. This is because there are yet other services that make a connection between the Surface Web and Onion Services.
But think about it. Using a service like this means that you are letting one of these services sit in between your computer and Tor to handle the connection for you. There goes your anonymity.
We don’t recommend using these services.
Who pays for all this?
Surprisingly, the US Government pays for a lot of it. According to CNBC International’s “What is the Dark Web?” video, the State Department and the Department of Defense provide 60% of the funding for the Tor Project. They support Tor so that dissidents worldwide have a secure place to organize and report on abuses. Various US government agencies use Tor as well.
Beyond the US government, several other organizations contribute. But the greatest number of contributions (if not total dollars) comes from individuals. Individuals contribute both with cash and by running Tor relays.
How do I get started?
If you are ready to give Tor a try, now’s the time. Follow the steps below, and you will be up and running on Tor is short order.
Decide Which Operating System to Use
Tor provides anonymity when using on the Internet. But if your Operating System is insecure, you are still vulnerable. If being a Tor user really does invite increased government attention, you may be more vulnerable than before.
You can run Tor on Microsoft Windows. But most people interested in privacy are moving away from Windows. Why?

Because Windows has such a large market share, it is the prime target for hackers. Because Windows has a history of being vulnerable to viruses, hackers, and all sorts of security problems. And because, at least with Windows 10, Microsoft grants itself permission to gather all sorts of information from your computer and record it in its own database.
A better choice would be to use a version of Linux. Most security professionals see Linux as more secure than Windows or even MacOS.
The choice is, of course up to you. But whichever Operating System you choose, make sure you install the latest security updates and use a quality antivirus/antimalware program.
We’re going to use Linux Mint for this example.
Download and Install the Tor Browser for Your Operating System
Go to the Tor Browser download page and click the Download button for the version for your Operating System.
Once the download is complete, click the sig link below the button to verify the Digital Signature of the package (follow the red arrow in the image below). This ensures that the Tor file has not been corrupted or hacked. If you don’t know how to do this, the Verifying Signatures page has instructions.
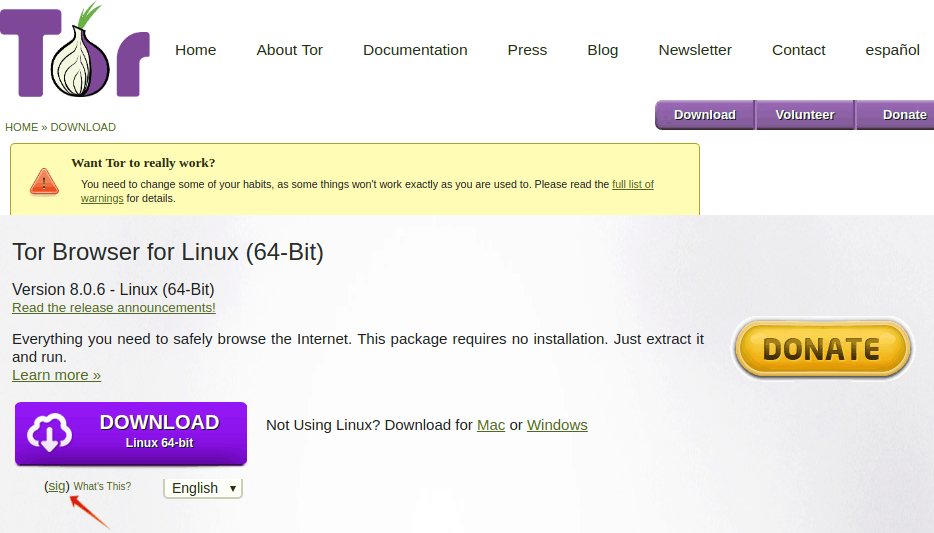
Once you confirm the Digital Signature, install the Tor browser normally.
Before you go any further, we strongly recommend you read the warnings and suggestions in the “Want Tor to really work?” section of the download page. If you follow the given advice there, it will make using Tor even more secure.
Start Browsing Privately with Tor!
If you followed the preceding steps, all you need to do is launch the Tor Browser. Expect to wait a few moments as the browser establishes a connection to the Tor network. After that, you should see something like this:
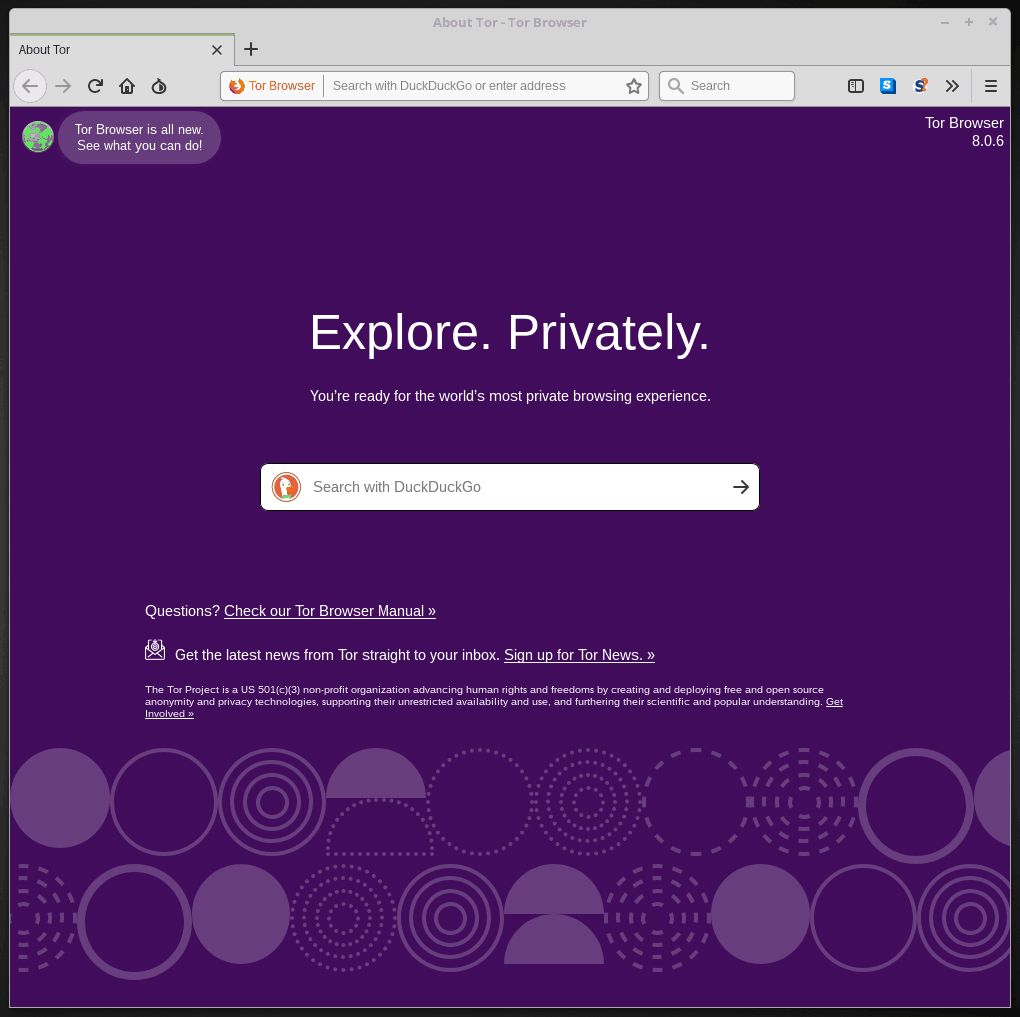
Before you do anything else, heed this warning: Some people claim that you should never resize the Tor Browser window from the default that it launches in. They say that doing so will make your browser stand out a bit from those of other users who have not changed the size of the window.
We don’t know whether this is something to worry about or not but wanted to throw it out there before you start playing with your shiny new Tor Browser.
Hey! What about some indexes to get us started?
Here is an Onion Service index to get you started.
We can’t vouch for these guys beyond saying that they seem to be legitimate and as of 5 March 2019, they were still online.
Should I use Tor?
We don’t want to weasel on you, but that depends. It depends on what you do online, where you live, and how much you care about protecting your privacy. To help you figure this out, we’ve put together a table of Pros and Cons of using Tor from the privacy perspective:
Privacy Pros and Cons of Tor
| Pros | Cons |
| Tor provides anonymity | Tor anonymity isn’t perfect |
| Tor is free | Tor has been hacked |
| Tor is easy to use | Using Tor might make you more interesting to government snoops |
| The more people use Tor the safer every user is | Browsing with Tor is slower than using with a regular browser |
| Tor gives you access to Onion Services you otherwise couldn’t reach | Tor lets you get into areas of the Internet where bad stuff happens |
The rest is up to you. But remember, this isn’t an all or nothing affair. If you want, you can use your regular browser for regular stuff, and use Tor for things like banking and investigating that sensitive medical condition you don’t want anyone to know about.
Good luck, and stay safe!
P.S – For even more privacy, read our Tor vs VPN guide.
Or if your interested in an alternative to Tor, check out our article on ‘What is I2P‘.
References
- Definition of DNS
- What is the Surface Web?
- What is the Deep Web?
- What is Linux?
- What is a Digital Signature?
- What is Internet Privacy?
- What is Encryption, and how does it work?
- Onion Routing Explained
- Techopedia’s definition of Data Packets
- Tor’s Guard Relay Explained
- Tor’s Middle Relay
- Tor’s Exit Relay Visualization

![A Beginner’s Guide to Monero – What Is XMR? [Updated 2023]](https://cd.blokt.com/wp-content/uploads/2019/04/Beginners-guide-to-Monero-2-218x150.png)

![Best 5 Bitcoin Sports Betting Sites [2023] (Analyzed & Approved) Best Bitcoin Betting Sites](https://cd.blokt.com/wp-content/uploads/2020/05/best-bitcoin-betting-sites-218x150.png)

