VPNs are powerful tools for securing your online privacy. Multi-hop VPNs take this to the next level. By adding in additional VPN servers (or even using multiple VPN services together), they can increase the strength of your security and improve your privacy.
In this article, we will look at how multi-hop VPNs work. We’ll also look at the pros and cons of the two classes of multi-hop VPN, and mention a few services that offer ready to use multi-hop solutions.
How a Multi-Hop VPN Works
At the most abstract level, a multi-hop VPN works by passing your message traffic through multiple rounds of encryption, thereby making it harder for someone to break through the security and violate your privacy. In practical terms, this means that your message traffic will pass through at least two VPN servers instead of one as in a regular VPN.
We can go into more detail about exactly how this works, but before we do, we need to talk about the two types of multi-hop VPN.
Types of Multi-Hop VPN
Since a Multi-Hop VPN involves the use of more than one VPN server, there are two ways to implement them. One approach is to use a single VPN service that supports routing your message traffic through two or more of its own VPN servers. The other approach is to use two or more VPN services and pass your message traffic through them in sequence.
In the next couple of sections, we will go into more depth on these two classes of multi-hop VPN. This will make figuring out the pros and cons of each much easier.
One VPN Service, Two or More VPN Servers
A single VPN service that passes your message traffic through two or more of its own VPN servers is the most common way to implement a multi-hop VPN. This type of multi-hop VPN is sometimes referred to as a “cascade” or a “cascaded connection.”
In a regular VPN, messages from your computer travel like this:
- Step 1: The message gets encrypted by the VPN software on your computer, then passed to a VPN Server.
- Step 2: The VPN Server restores the document to its original state but changes the IP address. Instead of the IP address of your computer, the message gets the IP address of the VPN Server.
- Step 3: The VPN server sends the message to its final destination. It arrives in its original form except that it appears to have originated at the VPN server instead of your computer.
In a cascaded connection style VPN, the first two steps are the same, but then the message gets encrypted again and is sent to another VPN Server. There it is decrypted, the IP address changed to that of the second VPN server, and it is passed along to its destination. Let’s call the first VPN server in the chain the entry server and the last VPN server in the chain the exit server.
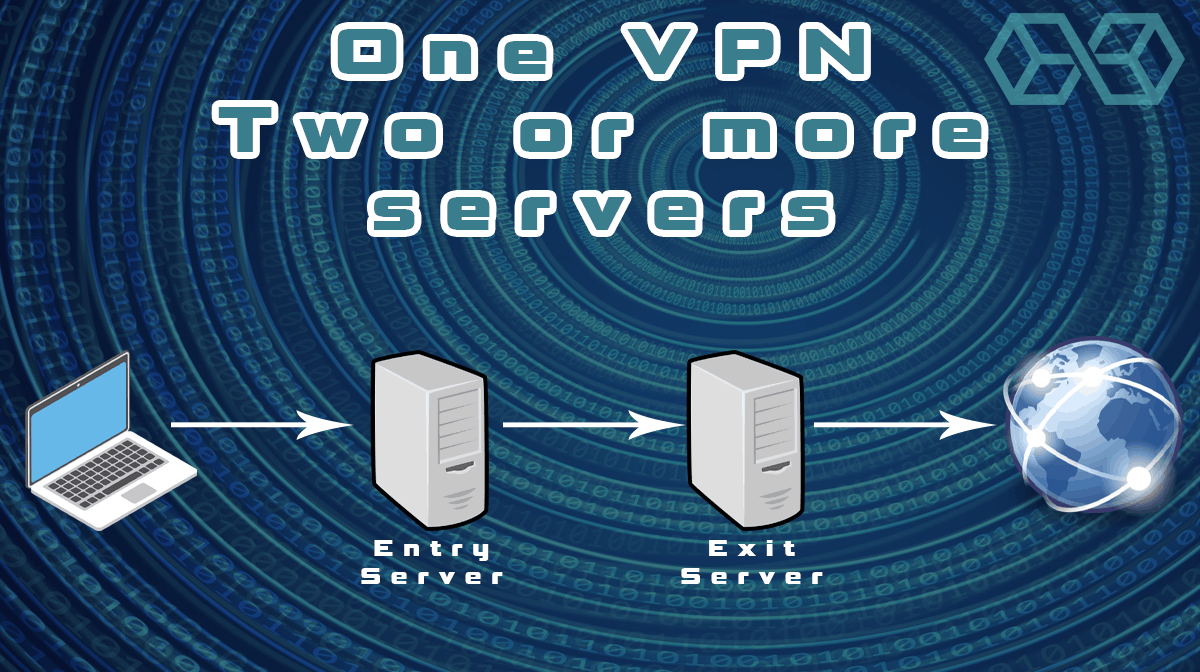
Here’s an example of the full process using just two VPN servers:
- Step 1: The VPN software on your computer encrypts the message, then passes it to the entry server.
- Step 2: The entry server restores the document to its original state but changes the IP address. Instead of the IP address of your computer, the message gets the IP address of the entry server.
- Step 3: The entry server encrypts the message (including its new IP address) again and sends it to the exit server.
- Step 4: The Exit Server restores the document to its original state but changes the IP address. Instead of the IP address of the entry server, the message gets the IP address of the exit server.
- Step 5: There, the message is decrypted and sent to its final destination with the original content and the IP address of the exit server.
With this approach, the destination website sees your messages as originating at the exit server. And the exit server has no way to know who you are. When it decrypts the message, all it sees is your original text and the IP address of the entry server.
Even if someone had complete control of the exit server, they wouldn’t be able to figure out your real IP address. The entry server would still protect you.
Several popular VPN services offer cascaded connections under one name or another. We will look at a few of them later in this article.
Two VPN Services
While the standard multi-hop VPN setup definitely increases your security and privacy, it is still theoretically vulnerable. Since everything that happens is under the control of a single VPN service, someone who gains control of the service might be able to cut through all the protections that it provides.
To get around this, you could create a multi-hop connection using two different VPN services. In this way, an attacker would need to compromise both VPN services to get full access to your message traffic. We will refer to this as a multi-VPN connection or solution.
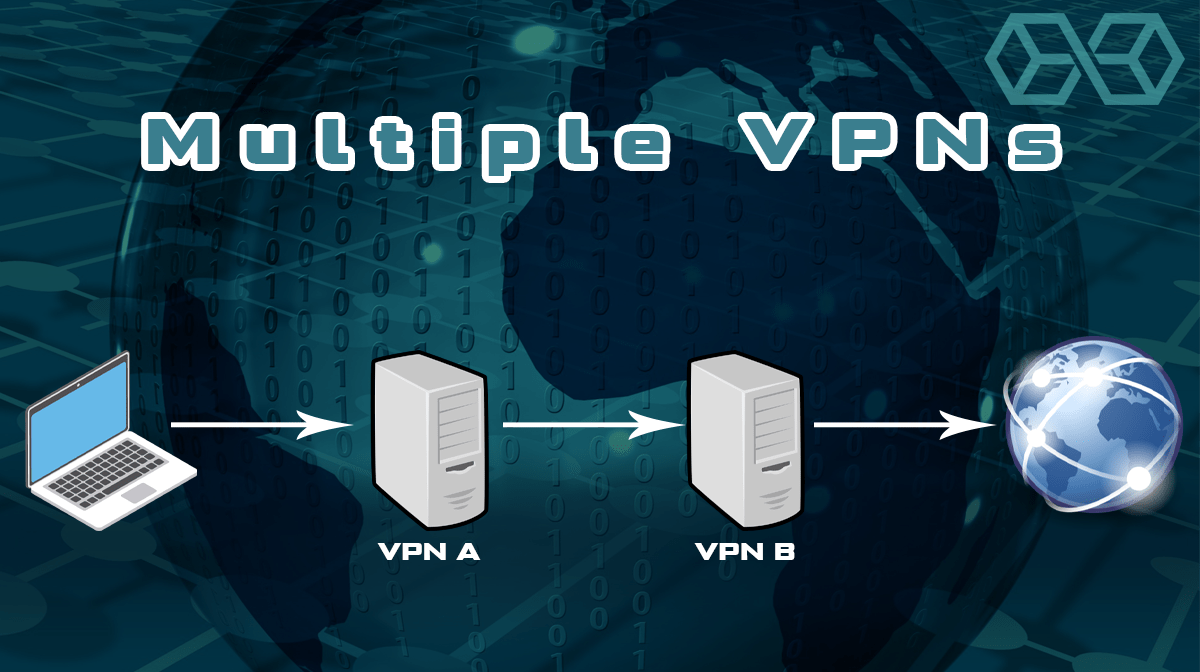
We don’t know of any commercially available multi-VPN chains like this. If you want this kind of protection, you need to build it yourself. Without getting into the technical details, here are a few ways to create a nested chain connection:
- Install one brand of VPN on a router, and a different brand on any devices you want to protect. Any message traffic from the device will be protected by both VPNs whenever the device VPN is active.
- Install one brand of VPN on a device and the browser extension for another brand in the web browser. Any message traffic from the browser will be protected by both VPNs whenever both VPNs are active.
- Install one brand of VPN on a device, and a different brand in a virtual machine (VM) running on the device. You can use a free virtualization solution such as VirtualBox for this. Any message traffic from applications running in the VM will be protected by both VPNs whenever both are active.
Are These All the Options?
No, these are not all the options. Some VPNs let you cascade 3, even 4 VPN Servers before the messages exit the VPN network. And it is possible to chain together more than 2 VPN Services. You could probably even set up a system that automatically switches servers within the VPN network (similar to the way Tor changes things up every few minutes).
But for the purposes of this article, we just need to consider the two classes of multi-hop VPN: cascaded connections (multiple servers in one VPN) and Multi-VPN connections.
Pros and Cons of a Cascaded Chain Connection
Multi-Hop VPNs that offer cascaded chain connections are great for providing extra protection. But like anything else, using them has benefits and drawbacks.

Let’s see what the pros are, again using just an entry server and an exit server:
Pros of a Cascaded Chain Connection
- Increased security and privacy compared to a regular VPN Service. An attacker who gets control of only one server in the chain will not be able to see both your message and your IP Address.
- Anyone monitoring your Internet connection can see that you are connected to the entry server in the chain, but the IP address of the exit server is hidden from them. This makes it much harder to run any kind of traffic correlation attack against your traffic.
- You can bypass more kinds of Internet censorship. Say the United States decides to block all connections to Russia, but you need access to content that is only available to users in Russia. Choose an Entry Server that isn’t blocked by the United States and an Exit Server that is located in Russia. That should get you around the censorship on both ends of the connection.
Now let’s look at the cons.
Cons of a Cascaded Chain Connection
- More processing power is needed on your device than with a standard VPN since the device needs to encrypt/decrypt everything twice.
- The latency of the connection will likely increase because the additional physical connections between servers will take longer for messages to traverse.
- With more servers in the chain, there is a higher chance that one will slow down the connection due to the power of the server or a large number of current users.
- Not many services offer a cascaded chain connection.
- If an attacker has control of your VPN Service, it could monitor the entire connection and record your messages, your IP Address, and the sites you connect to.
Pros and Cons of a Multi-VPN Connection

And now for the pros and cons of a nested chain connection, assuming you build it with only two VPN Services:
Pros of a Multi-VPN Connection
- If an attacker gets control of the second VPN service in the chain, they will still not be able to see your messages or IP address because the first VPN Service will still protect you.
- Anyone monitoring your Internet connection can see that you are connected to the second VPN Service in the chain, but won’t be able to see that your messages already passed through the first VPN service. This makes it much harder to run any kind of traffic correlation attack against your traffic.
- Any website or service you connect to can see that your messages pass through the second VPN service in the chain, but won’t have any information on the first VPN service. This also makes it much harder to run any kind of traffic correlation attack against your traffic.
Now let’s look at the cons.
Cons of a Multi-VPN Connection
- You may need far more processing power on your device than with a standard VPN service. Worst case the device needs to run a VM and two complete sets of VPN software.
- The latency of the connection will increase because of the delays caused by messages traversing two full VPN services.
- If an attacker has control of the first VPN service, they could monitor the entire connection and record your messages, your IP address, and the sites you connect to.
- Setting up a multi-VPN connection is much more complicated than using a cascaded chain connection from a VPN service.
- A multi-VPN connection will probably be more expensive than other solutions since you must subscribe to all of the VPN services in the chain.
Some Popular VPNs with Multi-Hop 700w
Now that we’ve seen what multi-hop VPNs are all about let’s look at a few VPN services that implement multi-hop connections. These will all be cascaded chain connections since we know of no one offering a commercial nested chain service.
Nordvpn
Probably the most flexible multi-hop solution is available through Nordvpn.
 NordVPN is one of the world-leading VPN Services. As is befitting of that standing, they too offer a Multi-Hop solution. Called Double VPN, it creates a two-server cascaded chain. On their Double VPN page, they cover the basics of the solution, as well as list the types of users they think would benefit from using Double VPN, along with types that should not use it.
NordVPN is one of the world-leading VPN Services. As is befitting of that standing, they too offer a Multi-Hop solution. Called Double VPN, it creates a two-server cascaded chain. On their Double VPN page, they cover the basics of the solution, as well as list the types of users they think would benefit from using Double VPN, along with types that should not use it.
To learn more about NordVPN’s Double VPN solution, click here.

Read our NordVPN Review here.
SurfShark
SurfShark is an up-and-coming VPN Service that has been around less than two years. Even so, it offers a number of advanced features, including its multi-hop solution, which it calls MultiHop. Like the examples in this article, MultiHop is limited to two manually-selected VPN servers.
To learn more about SurfShark’s MultiHop solution, click here.
Read our SurfShark Review here.

Conclusion
When a standard VPN connection isn’t secure or private enough for you, there are stronger, more exotic solutions you can try. But the stronger you go, the more drawbacks you get along with those benefits. For example, using the Tor browser could really boost your anonymity, but burdens you with a large speed hit and incompatibility issues.

A multi-hop VPN gives you additional security and privacy without requiring you to get too exotic. In this article, we talked about what a multi-hop VPN is, how they work, along with their pros and cons. We wrapped up with a short discussion of some of the popular VPN Services that support this kind of solution.
We really recommend checking out our 4000 word+ best vpn guide for a list of VPN’s that really meet our strict privacy criteria. Most support multi-hop and all of them have a stellar no logging attitude.
If you want a VPN to meet a certain criteria , see our best VPN lists in torrenting, Gaming, Iphone, Android & Netflix.
References
- Why should you care about Online Privacy?
- Advantages of a Cascaded VPN Connection
- What is encryption, and how does it work?
Disclosure: Blokt strives to provide transparent, honest reviews, and opinions. The writer of this article is a user of the product(s) or service(s) mentioned in this article and was not influenced by the respective owners.
We rarely run ads, but sometimes earn a small commission when you purchase a product or service via a link on our site. Thank you kindly for your support.
Read more or donate here.


![A Beginner’s Guide to Monero – What Is XMR? [Updated 2023]](https://cd.blokt.com/wp-content/uploads/2019/04/Beginners-guide-to-Monero-2-218x150.png)

![Best 5 Bitcoin Sports Betting Sites [2023] (Analyzed & Approved) Best Bitcoin Betting Sites](https://cd.blokt.com/wp-content/uploads/2020/05/best-bitcoin-betting-sites-218x150.png)

