Introduction
You’ve probably seen the recent headlines regarding the Coinhive mining script. It has been spotted on numerous websites and even dozens of apps in the Google Play store. While the Coinhive script is undoubtedly being abused, the term “malware” is not necessarily an accurate or fair description; it is merely a browser mining script. There could come a day when users are happy to allow access to a portion of their processing power while visiting a particular website, in exchange for an absence of intrusive ads. Malwarebytes recently labeled the script as malware much to the dismay of some.
A more fitting description for the more sinister usage of this script would be:
Bad actors are utilizing existing exploits to insert the Coinhive script into unsuspecting webmasters code.
We decided to take a look at the current reach of the Coinhive script. Just how many websites are affected, and are there any commonalities between those sites?
Discovering The Affected Sites
As the Coinhive script is run from a centralized location, it’s rather easy to locate the sites that are using it, whether they are aware of the code or not. Sites running the script usually have the following code embedded in their website (along with some similar variants):
<script src="https://coinhive.com/lib/coinhive.min.js"></script>
So all we need to do to find these sites is scan the source code to check for references to the Coinhive script. We scanned our go-to databases, which contains recently updated website source code for more than 200 million domains. We then ran a check for the Coinhive script against the live websites and got the following number of hits:
- 8,786 domains
It would be safe to assume this estimate is on the low side also due to a few factors:
- We are only checking the website homepage, not all pages
- 99+% of checked sites are root domains (not subdomains)
- Some sites may have been unavailable at the time of checking
- Some sites may require users to log in
- We didn’t parse every single website in existence!
Note: The domains and metrics published in this post were collected on 10th November 2017. The specific websites which are running the Coinhive script and the metrics of these domains will change as time passes. We’ll aim to update this post periodically.
Grabbing the Metrics
So now we have a nice list of affected domains, let’s parse some metrics. We’re going to extract the following information for each domain:
- TLD (Top Level Domain such as .com, .net, .co.uk etc.)
- Language
- CMS or Framework (Content Management System, such as Drupal, WordPress, etc.)
- Website Category
- Alexa Rank
- Google Safe Browsing Status
- Hosting IP Address
- Hosting Geolocation
- Majestic SEO Rank
- Estimated Search Engine Traffic
- Facebook Shares
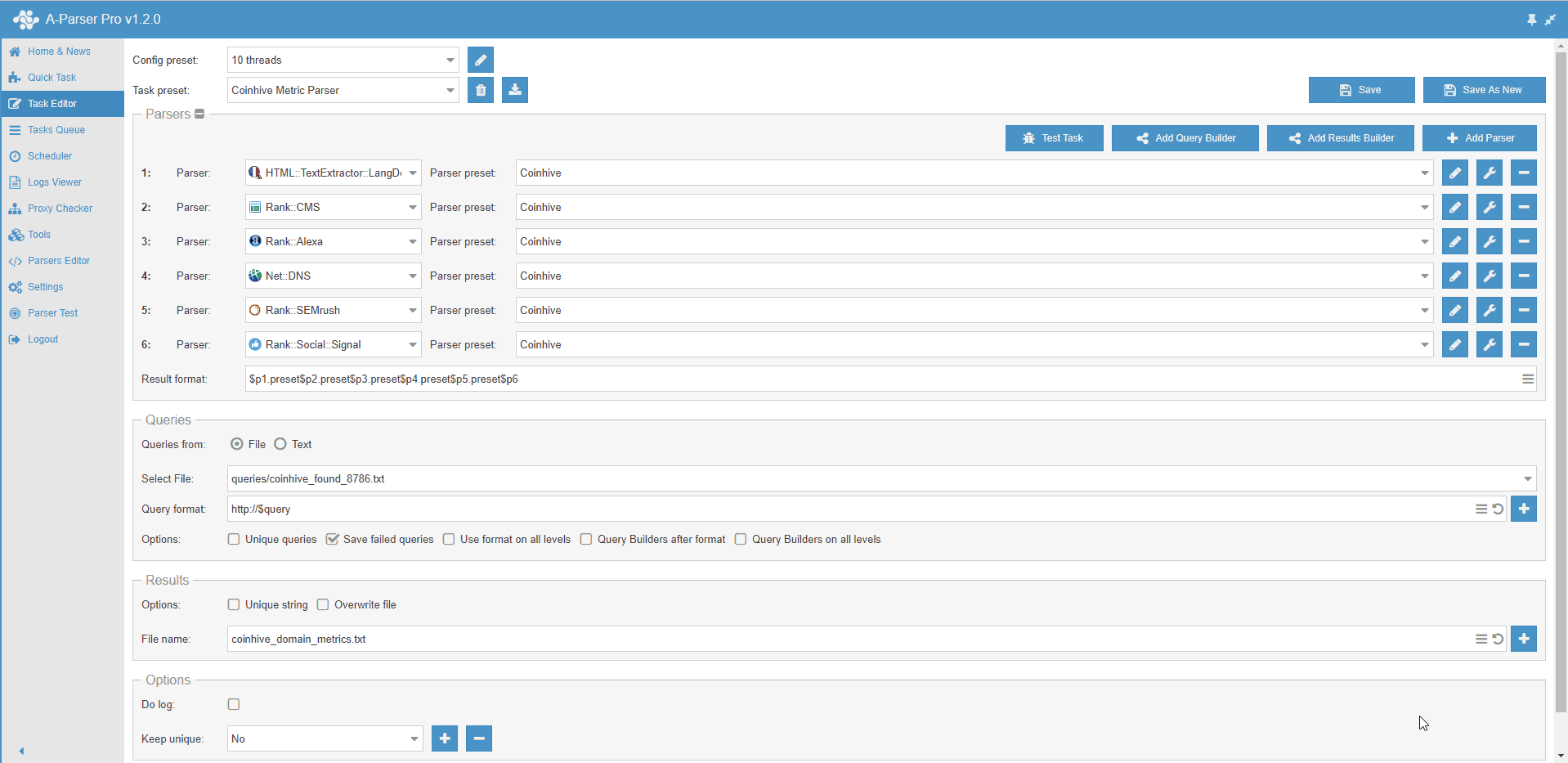
The only tool, in our eyes, for a such a job is A-Parser, a massively versatile parsing tool that can parse most of the metrics we need out of the box and is hugely customisable.
Here are some other sources we will use to collect our metrics:
- We’ll use the Webshrinker Category API to obtain the Website Category.
- We’ll use John Kurkowski’s tldextract to extract TLDs.
- We’ll use A-Parser’s “Net::DNS” parser to retrieve the IP address and then feed this into the ipinfo.io API using a custom parser, within A-Parser, to collect the Website Hosting Location.
- We’ll use the Majestic API to collect their TF (Trust Flow) and CF (Citation Flow) SEO data.
- We’ll use the Safe Browsing Lookup API (v4) to collect Safe Browsing data.
After a quick test of our settings, we put A-Parser to work and began working on scripts for the non-supported metrics above.
Initial Results
Down the rabbit hole we go! The results from our parsing are displayed in the table below.
Coinhive Analysis Table
Immediate Observations
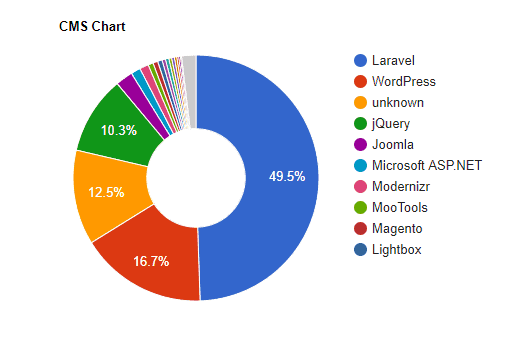
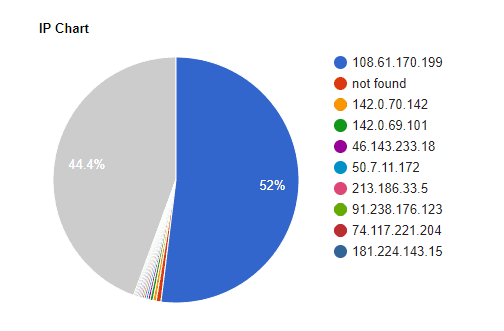
On looking into our data, one thing that becomes immediately apparent is that there are an abundance or .ir (Iranian) domains, all hosted on the same IP address, using the same PHP Framework, Laravel.
That’s 4,462 (50.8%) of the domains on .ir TLDs, 4,565 (52%) on the 108.61.170.199 IP and 4,347 (49.5%) running Laravel Framework. It would be safe to assume, at this point, that the majority of the domains with any of these metrics are connected.
Let’s run a simple MySQL query to verify:
SELECT COUNT(*) FROM `coinhive_table` WHERE `tld`='ir' AND `cms`='Laravel' AND `ipaddress`='108.61.170.199';
4205 Results
There are a couple of things to note at this point:
- Some single entity is likely responsible for these 4,205+ Iranian domains that are running the script.
- These domains should probably be removed to examine our data further and get a good overall picture, more on this later.
The Iranian Connection
These domains are worthy of some more digging, let’s take a look at some example domains:
0002.ir
0004.ir
0005.ir
...
aaaaaa.ir
aadd.ir
aaii.ir
...
zbd.ir
zbf.ir
zbk.ir
As you can see, these look like they’ve been registered using a simple script with 0-9 and a-z entries.
Here’s what the websites look like, those that we spot-checked were identical except for the domain name:
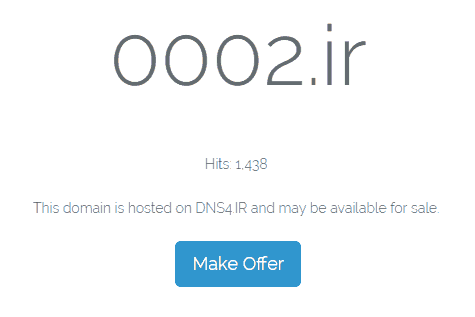
This is beginning to look less like hacked/exploited domains and more like something else! All of the domains are for sale and parked via dns4.ir, the WHOIS details of this website match the WHOIS for many of these domains.
Foul play is not apparent, but a few questions are indeed raised. Principally, how is someone profiting from registering 4,000+ domains, at around $25 each? The domains show no estimated search traffic, no inbound links, and very few show any social activity. Whether there is something ominous going on or this is simply an elaborate domain parking setup is currently unknown. We are leaning towards the idea that this is just monetization of parked domains, set up by a domainer.
Filtered Results
We cleaned the .ir domains from our results and took another look at the data; we are now looking at 4,324 domains.
Filtered Coinhive Analysis Table
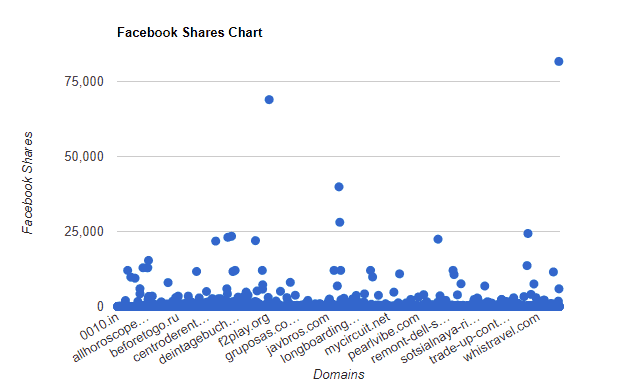
There are some domains with a significant number of Facebook shares, the majority under 5,000, and a large percentage of sites with none at all; 2,194 domains (50.7%.)
Two domains had values too large for our graph:
- piratebay.red – 737,526,323 Shares
- mobileoffers.me – 7,536,447 Shares
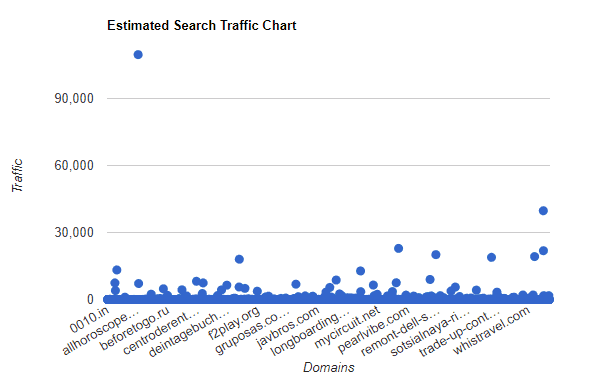
Estimated Search Traffic
This chart displays domains estimated search traffic. As you can see, there are some domains with significant traffic. However, 3,636 domains (84.1%) have no predicted traffic at all.
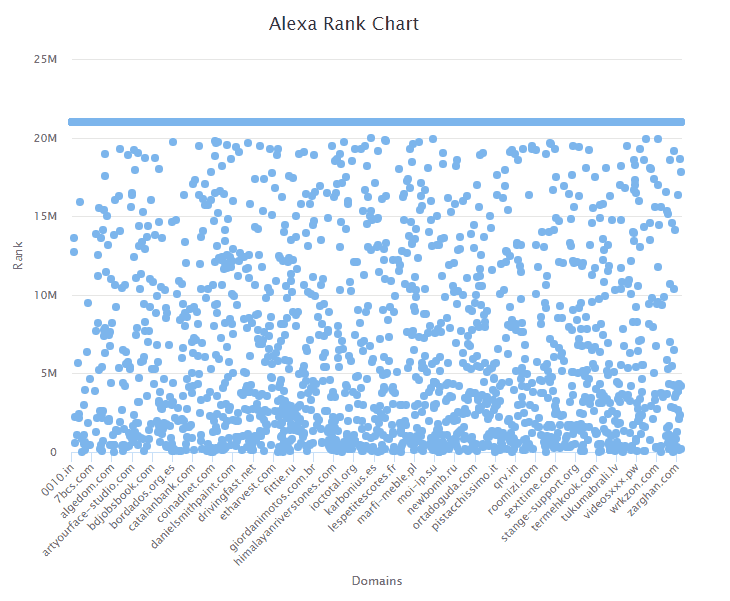
Alexa Rank (Lower is Better)
Where domains are actually scored, the Alexa Rank of the websites is quite evenly spread. There is a significant percentage of these domains with a score of under 5 million (the top 5 million websites in existence, according to Alexa). Again, however, a large percentage of domains had no ranking. We set these non-ranking domains to have a score of 21,000,000, so they can be visualized here (Alexa only scores the top 20 million websites). There are a total of 2,678 (61.9%) domains with no ranking.
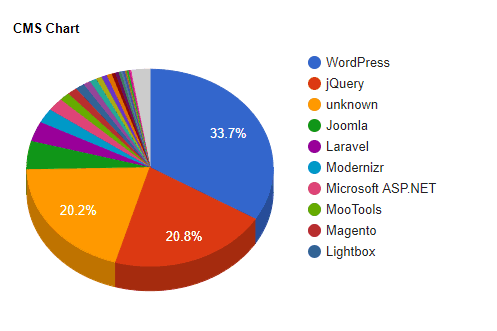
CMS Affected
The largest number of domains are running WordPress, which is unsurprising, considering it’s one of the more popular in existence. It is, however, notorious for being regularly hacked.
At this point, it’s unclear whether these WordPress domains are compromised or not. To establish this would require further investigation. We could look into the WordPress versions in use and analyze individual sites to determine this, something we might tackle later.
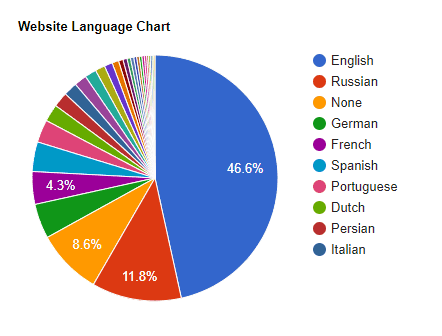
Website Languages
English is the main language in use, but there is a surprisingly high number of websites using Russian. This could be due to Russian webmasters being more versed on cryptocurrencies and the technology than your average webmaster.
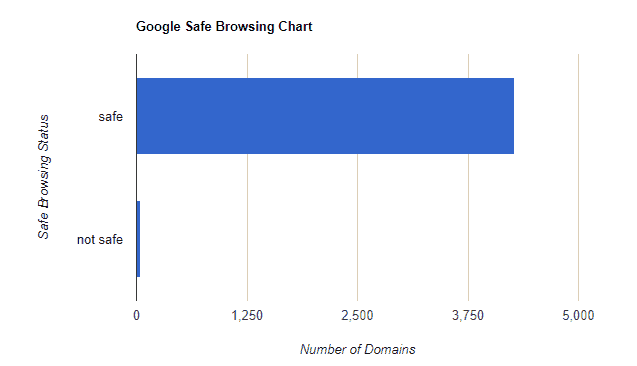
Google Safe Browsing Status
The vast majority of websites are seen as safe by Google, with only 47 sites marked as unsafe. This goes to show that Google, for now, is not treating the Coinhive script as malware.
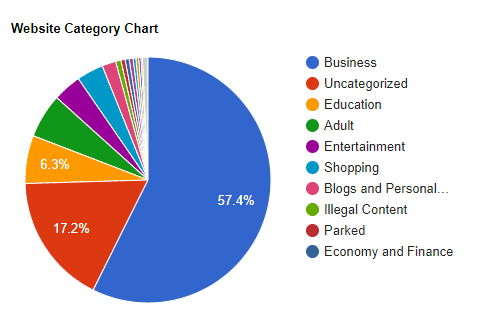
Website Categories
57.4% of the websites are categorized as business sites. We’ve checked some of these sites and feel that this category is a somewhat broad, so the data here is not of much use. A fair number of adult websites also appear to be utilizing the script, perhaps doing their best not to interrupt(!) their visitors with ads, or using Coinhive as an additional income stream.
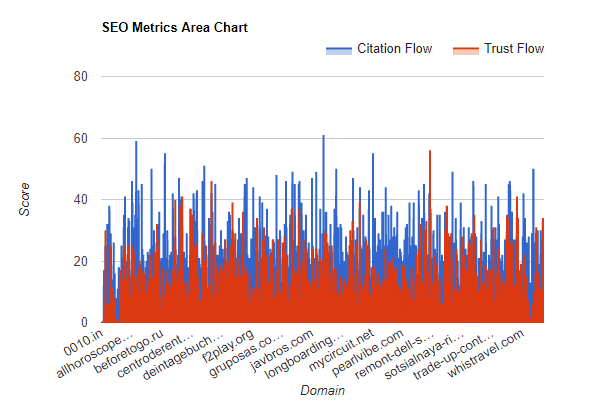
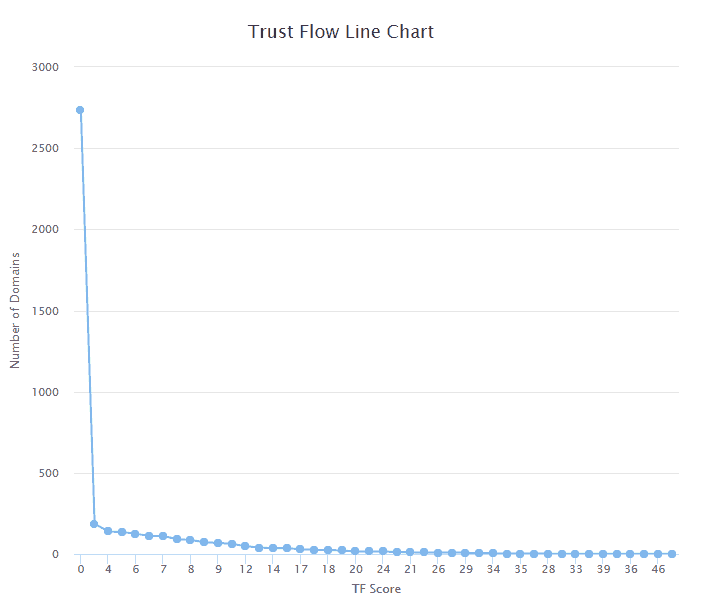
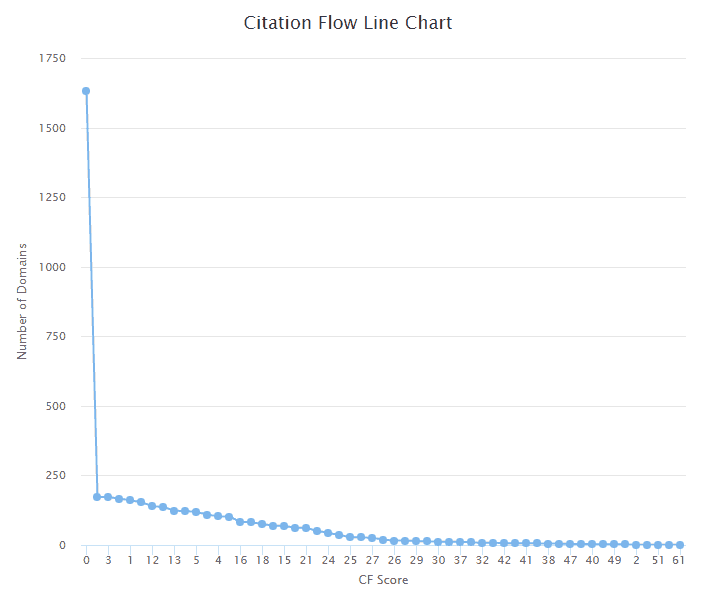
SEO Metrics
The SEO metrics we used are TF (Trust Flow) and CF (Citation Flow) from Majestic. These are both scored on a scale between 0-100. To summarize these two metrics:
- Trust Flow is an indicator of how trustworthy the backlinks pointing to the site are. If a site is linked to from trusted websites, the score will be high, if it is linked to from questionable websites, the score will be low.
- Citation Flow is used to determine how influential a website is based on how many incoming links it has.
The sites which have scored higher than 0 appear to have a relatively even distribution of scores from Majestic. To break down these two metrics further we’ve also created some line charts:
As you can see, the majority of the sites have a score 0, with far more sites scoring on the lower end of the scale.
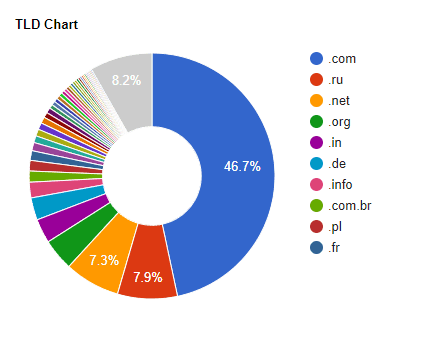
TLDs Affected
A large number of .com domains, but again, a significant number of .ru (Russian) domains. There is also a notable number of .in (Indian) and .de (German) domains.
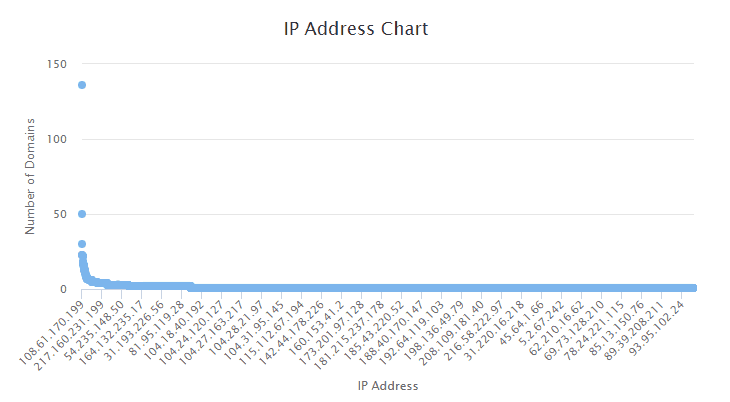
IP Addresses Affected
There is a total of 2,936 IP addresses in our data. We can further analyze if specific IP addresses are hosting multiple affected domains below:
As revealed in the chart, some IP addresses are hosting many websites. We can see that the owner of the .ir domains, using the IP 108.61.170.199, still has some domains in our data hosted on different TLDs.
The other IPs which host the script on multiple domains could be explained by one of the following:
- Webmasters are hosting multiple domains on single servers and installing the script on many of their domains.
- Web hosts have been compromised, and multiple websites on the hosts are “infected.”
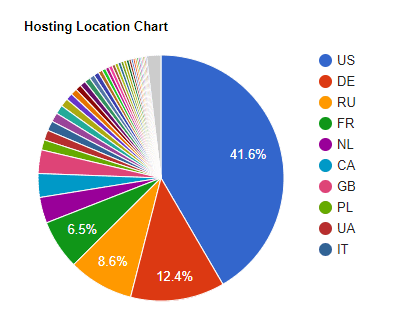
Hosting Locations
The majority of sites running the Coinhive script are hosted in the US, with Germany and Russia having notable numbers also.
Noteworthy Data – Trusted & High Traffic Sites
Lingerie Website
- penelopelingerie.fr
A seemingly popular online lingerie store for French customers. First added to the Wayback Machine in April 2013 with the same physical store address on the site as they have currently.
- Facebook Shares: 3,177
- Alexa Rank: 3,026,277
VERDICT: Probably hacked
Musician
- vintageculture.com.br
This website appears to be the main for a Brazilian Musician, “Vintage Culture.” Apart from the Coinhive script, the site appears to be functioning correctly. It is hard to determine whether this site is running the script for profit or if the script has been placed maliciously.
- Facebook Shares: 24,341
- Alexa Rank: 1,959,414
VERDICT: Unknown
Google Blogs
- sohoandroid.blogspot.com
- rickandmortyfullhd.blogspot.com
- joatamon.blogspot.com
- ilikewarp.blogspot.com
- piliday.blogspot.com
- hentairpgmaker.blogspot.com
- proboxnatv.blogspot.com
- farmersnetly.blogspot.com
- i-ptv.blogspot.com
- ozlemsencanblog.blogspot.com
- androidrepublica.blogspot.com
- angiofoods.blogspot.com
- megavideotunisie.blogspot.com
- adrenetgames.blogspot.com
- downloadsroat.blogspot.com
Interestingly, Google’s platform, Blogger/Blogspot, has multiple subdomains which are running the coinhive script. It appears that users can reference external Javascript, so they are able to create “spammy” blogs on the Google platform and use the Coinhive script to monetize them.
- Facebook Shares: 0 to 766
- Alexa Rank: Unranked to 209,635
VERDICT: Added by users
Filesharing Sites
- piratebay.red
- kickass.cd
- alluc.ee

Pirate Bay is openly using the coinhive script as a method of monetization. It would be safe to assume that the same can be said about the other file sharing websites which we found.
- Facebook Shares: 2,437 to 737,526,323
- Alexa Rank: 16768 to 2214
VERDICT: Added by webmasters
Government Sites
- secheep.gov.ar
- cultura.rj.gov.br (Appears to have been cleaned up now)
Quite the shocker! Two government websites were found to be running the coinhive script. The Brazilian government website appears to have since removed it, but it still running and viewable in the source code on a website run by the Argentinian government.
We’re unable to confirm whether this was placed maliciously, although, you’d think any website running on the government servers should be adequately secured. You have to wonder whether the Argentinian government is profiting from running Coinhive.
- Facebook Shares: 10 to 23,424
- Alexa Rank: 949,052 to 889,516
VERDICT: Unknown
Educational Institutes
- udc.edu.mx
- lsu.edu.ph
- uaf.edu.mx
- florida.edu.vn
- aplusenglish.edu.vn
- isquareit.ac.in
- stieieu.ac.id
- farzanegan.ac.ir
A shocking number of educational institutions have the coinhive script present on their websites. Again, it’s hard to determine whether these websites are doing so knowingly. Any user visiting these sites running Malwarebytes Pro would see a popup notification showing that the script was blocked, so you would think this would have been reported by now.
- Facebook Shares: 0 to 1,276
- Alexa Rank: Unranked to 996,287
VERDICT: Unknown
Github Subdomain
- akagi201.github.io
This GitHub subdomain is redirecting to an “infected domain.” The user has set up a subdomain on GitHub and rather than placing the code directly, has redirected the GitHub site to a domain they control. This domain has the coinhive code present.
- Facebook Shares: 0
- Alexa Rank: Unranked
VERDICT: Added by user
Summary
Some key points to take away from our analysis are as follows:
- The majority of trustworthy sites or sites with significant traffic that are running the script are doing so, either intentionally or as the result of users adding the script to their page. There is a chance that some of these have been hacked but at this point, this is hard to prove.
- Some major sites have likely been hacked
- The majority of the other sites running the script have so little traffic that their disruption for users is probably insignificant.
- Domainers parking domains may be using coinhive for monetization. If Google’s stance changes towards Coinhive, this could devalue the domains in terms of future sales.
- Adult websites seem to be open to using the script.
- Government and educational websites are running the script.
- Subdomains on Google’s blogging platform are running the script.
- The is not a huge amount of evidence of hacking. Although many sites are likely hacked, the problem does not appear to be widespread.
As additional browser mining options become available, we are likely to see more and more websites utilizing scripts to monetize their users in the background and more hackers inserting the code into compromised sites. Some companies, such as NIMIQ, are currently developing browser specific cryptocurrencies.
Hackers and bad actors usually opt for the most anonymous form of income streams on hacked sites. This can be Affiliate Networks that ask no questions or dodgy SEO networks that will pay for backlinks on hacked sites. The ability to mine anonymously using compromised websites will be a reasonable option for hackers looking for untraceable payment for their crimes and webmasters looking to squeeze more income out of their sites.
Like cryptocurrency or the internet, the fact that browser mining can be exploited or used in sinister ways does not mean they shouldn’t exist. We should keep open minds and have constructive discussions about the future browser mining.



![How to Store & Secure Crypto on a Ledger Nano S [2020 Expert Guide]](https://cd.blokt.com/wp-content/uploads/2017/10/securing-background-218x150.jpg)
![Crypto OPSEC [2020]: Accounts, Cell Phones, 2FA & Security](https://cd.blokt.com/wp-content/uploads/2017/10/opsec-218x150.jpg)

