Biometric Recognition Systems are popping up everywhere today. Not long ago, systems like fingerprint scanners, retina scanners, and facial recognition were fanciful new tech from spy movies or SciFi novels. Now they are everywhere.
In this post, we’ll look at the field of Biometrics in general. Then we’ll look at three Biometric Recognition Systems that are in use today to see the privacy implications they bring. By the end of this post, you will have a good idea of the power of various Biometric systems and the Privacy threats they bring with them.
What Exactly Is Biometric Screening?
We’ve all heard the term biometrics. But what exactly does it mean? If you visit the Biometrics Institute, you can find the official definition of the term, as provided by the International Organization for Standardization (a.k.a. ISO)
ISO defines Biometrics (or more formally Biometric Recognition) as:
A Biometric Recognition System works by measuring one or more Biometric Characteristic to identify an individual.
ISO defines a Biometric Characteristic as a:
In plain English, Biometrics is a way for machines to recognize people based on characteristics such as the patterns of blood vessels in their eyes or the way they type.
In the last few years, Biometric Recognition Systems have popped up everywhere. You probably have one in your pocket right now. The fingerprint scanner that lets you unlock your smartphone with a touch is a Biometric Recognition System. This kind of biometric system is a great time saver that also serves to protect your privacy by making it harder for snoops to get into your phone.
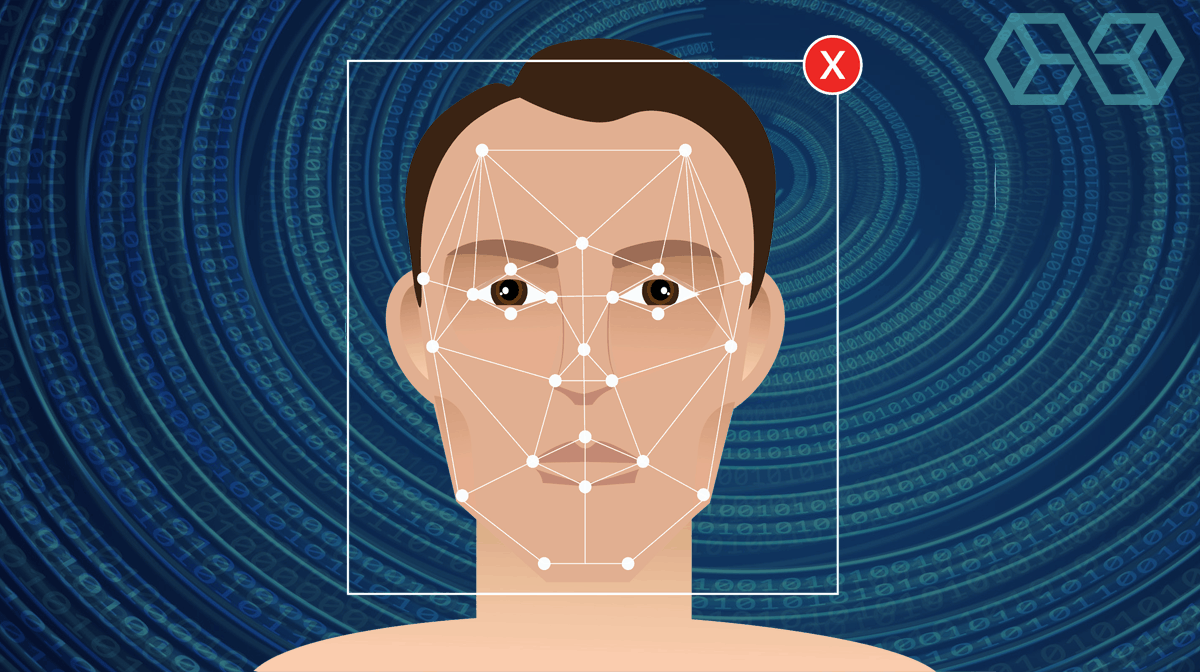
The Live Facial Recognition (LFR) system that the London Metropolitan Police have been testing is also a Biometric Recognition System. But this one scoops up personal information by the gigabyte and reduces personal privacy by alerting police to stop and question people who the system thinks that looks like known criminals.
In this article, we’ll look at various Biometric Recognition Systems, how they work, and what kind of impact they are likely to have on our privacy as their use becomes more widespread.
Types of Biometrics
When we started work on this article, I (your author) was surprised by the number of human characteristics that are now being used by Biometric Recognition Systems. Here is an alphabetical list of those Biometrics, as described on the Biometrics Institute website:
- DNA
- Dynamic Signatures
- Ear Shapes
- Faces
- Fingerprints
- Finger Geometry
- Gaits
- Hand Geometry
- Iris Recognition
- Odors
- Retinal Veins
- Static Signatures
- Typing Styles
- Vein Patterns
- Voice (Speaker) Identification
- Voice (Speaker) Verification/Authentication
We aren’t going to attempt to explain all these Biometrics here. We will, however, talk a little bit about three of them that will feature in the rest of this article.
Fingerprint Scanners
Fingerprint scanners use the pattern of ridges and valleys (called minutiae) on the tips of your fingers to identify you.
Retina Scanners
Retina scanners use the pattern of veins in the back of your eye to identify you.
Facial Recognition Systems
Facial Recognition systems analyze your facial features and convert the data into a form that can be used to identify you. There are various approaches, including local feature recognition and eigenfaces.
We don’t have to get into the technical details of these Biometrics to realize one thing. Unlike passwords or PINs, Biometrics is not something that you can easily change. This can make them strong ways to protect your privacy, but can also lead to big problems as we will discuss later.
The Impact of Biometrics — Efficiency vs Privacy
Like every technology, Biometrics can be beneficial or harmful, depending on how it is used.
It is certainly more efficient to unlock your phone with a touch of your finger than by typing in some code or doodling some pattern on the screen.
Surely using a retina scanner to control access to a building is more efficient than paying a human guard to check IDs at the door.
And no doubt letting a facial recognition system scan passers-by looking for suspects is more efficient than police tracking down bad guys the old fashioned way.
But each of these types of efficiency has its own cost in lost privacy.
The Fingerprint Sensor on Your Phone
To unlock your phone with a fingerprint, you need to train your phone to recognize your fingerprint. It only takes a moment and seems like a very small privacy risk. Both Google and Apple use special hardware and software to analyze and store your fingerprint data on their phones. As Android Central puts it:
When you press your finger to the sensor, that special hardware and software decide whether or not it is a match. The only information that gets out of that hardware and software is whether or not there is a match. Apps don’t get to see your fingerprint. Nor do Google, Apple, or any of the manufacturers who build and sell the phones.
This seems about as benign a use of Biometrics as anyone could ask for.
Using Retina Scans for Authentication/Access
Retina scanners and other Biometric systems used in security applications (like entering your secret underground spy headquarters) can give you some strong security. Faking a retina scan calls for extreme measures.
However, retina scanners have significantly greater privacy issues than the fingerprint reader on your phone. That’s because these systems almost always contain more personal information than just your retina scan. And they are usually connected to other scanners and some central computer system.
Think about the logistics of this. Say you have a facility with three entrances, and 20 people who need access to the facility. At a minimum, you need the ability to remove people from the system if they quit, get fired, defect, get taken out by enemy agents, whatever. And to do that, you need to be able to identify their particular Biometric Characteristics. Flushing the system and retraining it with everyone who needs access any time there is a personnel change would be a real headache.
So you end up with a Biometric system that contains Biometric Characteristics for every person who needs to be authenticated at that particular entry point, along with some way to identify which characteristics belong to which person.

Because you have multiple entrances, you need to have all your Biometric systems connected to some central control point. Otherwise, you will need to train and manage the Biometric system at each entry point individually.
As a result, you now have more personally identifiable information (PII) about each person in a system that is centrally controlled but has links to multiple remote Biometric systems. This arrangement is far more vulnerable than the phone example. If someone hacks into one of the connections or subverts the person operating the central computer system, an awful lot of private information will be vulnerable.
Using Facial Recognition Systems to Scan Public Places
Combining Facial Recognition Systems with surveillance cameras in public places could really help police track down bad guys. Even wanted suspects need to go out in public sometimes. Instead of detectives laboriously trying to track down baddies one at a time, a system like London’s LFR can scan the crowds waiting for a suspect to wander by. A system like this could save the police vast amounts of time and effort.
But think about how this works. The system scans the faces of everyone who passes in front of the cameras to see if they match a database of suspects. If the system thinks it has found a match, it passes information to a police officer who decides whether or not to question the person. Here is a quote from the Metropolitan Police’s LFR website:
The officer compares the camera image and the watch list image and decides whether to stop and speak to the person. We always explain why we’ve stopped someone; we also give them a leaflet that explains how they can contact us to ask any questions afterwards.
The system will only keep faces matching the watch list, these are kept for 30 days, all others are deleted immediately. We delete all other data on the watch list and the footage we record.
Anyone can refuse to be scanned; it’s not an offense or considered ‘obstruction’ to actively avoid being scanned.”
In other words, everyone is a potential suspect. If the system thinks you look like someone on the watch list,
- An officer may stop you and interrogate you
- Your face is stored in the system’s database for 30 days
- It is up to you to actively avoid being scanned if you want to protect your privacy
What could go wrong? For one thing, the system was notoriously bad at identifying criminals. For example, it reportedly incorrectly identified 2,000 people as being criminals at a single soccer match in 2017. Another report claims that from 2017 to 2019, the system incorrectly identified innocent people as criminals from its database 96% of the time.
At least you wouldn’t get in trouble for actively avoiding being scanned. Right? That’s what the LFR website says. But according to the Mail Online, this is what can actually happen if you dare to refuse to be scanned:
The police stopped the man, forced him to stand for a photo, and fined him £90 for disorderly conduct. Despite what it still says on the LFR website, the Mail story pointed out that,
Asked about this particular incident, a Scotland Yard spokesman basically said that you could actively avoid being scanned, but if you do, police could consider that suspicious and stop you to question you.
In other words, wherever the police were testing this system, you had no real privacy rights. You were an involuntary test subject for an incredibly inaccurate system that could add your face to a database of information about criminal suspects.

As of August 2019, the Metropolitan Police trials of the LFR system are over, and the police are deciding whether to deploy the system operationally.
What happens if this system or one like it does go into operation across London or the entire UK? There are huge numbers of CCTV cameras across the country that could be connected to the system. It would have the potential to track everyone in the country as they go about their daily lives. The amount of information that could be captured is immense, creating what most people would consider an enormous invasion of privacy.
For the latest information on how this plays out, visit the Big Brother Watch Face Off-page.
A Full Range of Efficiency vs Privacy Tradeoffs
The preceding three examples of Biometric Recognition Systems neatly cover the full range of the tradeoffs between efficiency and privacy that these systems bring.
The Fingerprint Recognition System in a smartphone gives you a boost in the efficiency of using your phone with virtually no risk to your privacy. As far as we can discover, there is no way for data about your fingerprint to leak out of the special hardware and software your phone uses to record your fingerprint. This particular type of Biometric Recognition Systems seems to be all benefits with no downside.

The Retina Scanners used to secure your secret underground base are more of a mixed bag. They do make it easy for you to enter the base. They do keep out the bad guys unless they can take really extreme measures to get a copy of your eyeball.
However, to be practical, this kind of system will probably contain more personal and private information than the fingerprint scanner. It will also be more vulnerable to hacking or simple data theft than the system in your smartphone.
Assuming they can someday be made accurate enough to count on, Facial Recognition Systems like LFR have a very different profile. They could be very efficient for the government, and possibly very useful for society as a whole.
But for the innocent individuals scanned by these systems, there is only the prospect of a loss of privacy, with the specter of an all-seeing, all-knowing government monitoring everything they do and occasionally siccing the police on them by accident.

One other thing to keep in mind. As we mentioned earlier, Biometrics are fundamentally different than passwords or account numbers. If your password or account numbers get stolen, you can change them.
The more Biometrics are used, the more places our fingerprints or retina scans or other Biometrics will be stored. If they are stored somewhere, the odds are that sooner or later they will be stolen.
What the hell are we going to do when the bad guys have copies of our Biometric data? You can’t change your fingerprints or retinal blood vessels like you can with your password. Once someone can buy our Biometrics on the Dark Web for a few dollars, we are well and truly screwed.
Conclusion
Biometrics and Biometric Recognition Systems are only going to become more powerful and more common. This post just scraped the surface of what these systems can do. Even so, you have seen the kinds of tradeoffs these systems offer.

It falls on each of us to look beyond the flashy marketing of Biometric systems to see their cost in terms of lost privacy. It falls on our entire society to decide what data can be gathered, who can gather it, and what we are going to do when this unchangeable Biometric data gets stolen.
P.S – A note from Blokt.com:
If you are interested in protecting your personal privacy then there are a few things you can do right now.
- Get a vpn – A vpn protects you from snooping ISP’s and allows you to stream movies, download torrents, play in online casinos or trade in crypto exchanges. Check out our best vpn article for more info.
- Use a secure browser – Read our browser guide to get more info, but we really recommend brave browser.
- Block ads – Use an AD blocker!
References
- What is CCTV?
- What is Eigenfaces?
- What is Minutie?


![A Beginner’s Guide to Monero – What Is XMR? [Updated 2023]](https://cd.blokt.com/wp-content/uploads/2019/04/Beginners-guide-to-Monero-2-218x150.png)

![Best 5 Bitcoin Sports Betting Sites [2023] (Analyzed & Approved) Best Bitcoin Betting Sites](https://cd.blokt.com/wp-content/uploads/2020/05/best-bitcoin-betting-sites-218x150.png)

