In this post, we will look at one of the big privacy questions related to our smartphones and the apps that run on them. Are the apps that run on our smartphones stealing our personal data?

The short answer is yes, they are. Apps always ask for permission to look at this or that on your phone. But what happens to the data they acquire? And who, exactly, gets to see that data? The story is far more complicated than people commonly realize. So keep reading to find out what’s really going on.
What Does Data Mining Mean, Anyway?
It is easy to get confused when talking about this stuff, so let’s start at the beginning. What is data mining? According to Investopedia:
Digging in a bit further, data mining is the process of discovering new information by analyzing massive amounts of data. When you analyze enough data, patterns and statistics can emerge that wouldn’t otherwise be visible. Businesses will mine data gathered from customers to help them market their products better.
Here is a simple example. Upon analyzing sales data, a company might discover that most of their customers live in big, East Coast cities. Using that information, they might shift their marketing to cater to people who live in those cities.
Data Mining can be very powerful. In general, the more data used in the analysis, the better. So companies have large incentives to gather as much data as they can. This is where smartphones and smartphone apps come into the story.
Why Would You Want to Mine Smartphone Data?
If you want to learn about people, ask their smartphone. Our phones know so much about us that it is scary. These little devices are extremely powerful computers equipped with huge amounts of memory, an incredible set of sensors, and fast connections to the Internet.
It is sometimes hard to grasp the power of these little beauties.
- According to Processing Power Compared, the computers that guided Apollo 11 to the moon in 1969 had a 2 MHz processor with 4 KB of memory.
- In 1985, the new Cray-2 supercomputer was one of the most powerful computers in existence. It was capable of 1.9 GFLOPS (billion floating-point operations per second).
How do these numbers compare with our smartphones? I use a Samsung Galaxy S9+. According to AnandTech, the graphics processor alone on my phone has a theoretical maximum speed of 247 to 370 GFLOPS. That makes just the graphics processor in my phone close to 200 times faster than the Cray-2!
Then there is the memory. According to the original brochure, the Cray-2 featured 256 million, 64-bit words of memory (about 1 billion bytes of memory). My phone has 6 GB (6 billion bytes of memory) for apps and its operating system along with 256 GB of additional storage.
Modern smartphones are vastly more powerful than the world’s most capable computers from a few decades ago.
But what makes smartphones even more interesting for data mining is the rest of the package.

Your smartphone’s memory holds pretty much everything about our lives. We store our personal information in them: bank information, photos, private messages, everything.
Now throw in incredible sensors that didn’t even exist a few years ago, like multiple HD-quality cameras, GPS, biometrics, and so on. With these, our phones can accumulate all sorts of additional information about us. In particular, our phones know where we are and where we have been. As someone once said, “We may not know where we were or what we did last night, but our phones do.”
Since our phones know virtually everything about us, the big question becomes, “Who gets to see my personal data?” Of course, the apps that we enter data into get to see it, but who else does it go to. In many cases, the people who write the code libraries that app developers use to run ads on your phone (we’ll call them “third-party developers” for simplicity) also get to see your data.
Third-Party Developers Get My Personal Data?
Yup. Code libraries are pre-built chunks of computer code that developers can use to do standard functions (run ads in this case) without having to write the code themselves. This is a great way to build apps since it allows you to get them written faster. But some of these libraries are problematic.
In a 2018 interview by the Chicago Tribune, Jason Hong of the Human Computer Interaction Institute at Carnegie Mellon University explained that many apps access sensitive personal data because the third-party developers won’t let app developers use their code unless the app gathers that data and passes it along to the ad companies. As a result, your personal data gets shipped off to who knows where for use by the third-party developers and whoever they share it with.
Just last month, Burton Kelso, Technology Expert at Integral Computer Consultants, told MSN.com that:
And speaking of your phone knowing where you were last night…
According to the New York Times:
While this data is anonymized, it turns out to be pretty easy for companies to figure out who you are if they want to.
Imagine that the anonymized data shows something like this: A phone leaves your house, goes to where you work, then goes to a restaurant you frequent, then goes back to your house. It is a pretty safe bet whose data they’re looking at.
While it is easy to disable the location tracking features in our phones, doing so will cripple apps like Waze or Foursquare that need to know where you are to do their jobs.
They Send My Personal Data to Facebook Too?
Earlier this year, from this article in the Wall Street Journal, we learned that many apps take the personal data you enter into them and immediately send it to Facebook. This could happen even if you didn’t have a Facebook account!
Two of the apps tested by the Journal were Instant Heart Rate: HR Monitor, and Flo Health Inc.’s Flo Period & Ovulation Tracker. These apps used an analytics tool from Facebook, which, among other things, passed data back to Facebook for analysis and ad targeting. The following screen capture shows the Journal’s diagram of how even a non-Facebook user’s ovulation status could be entered into Flo Period & Ovulation Tracker, but wind up in a Facebook ad targeting database.
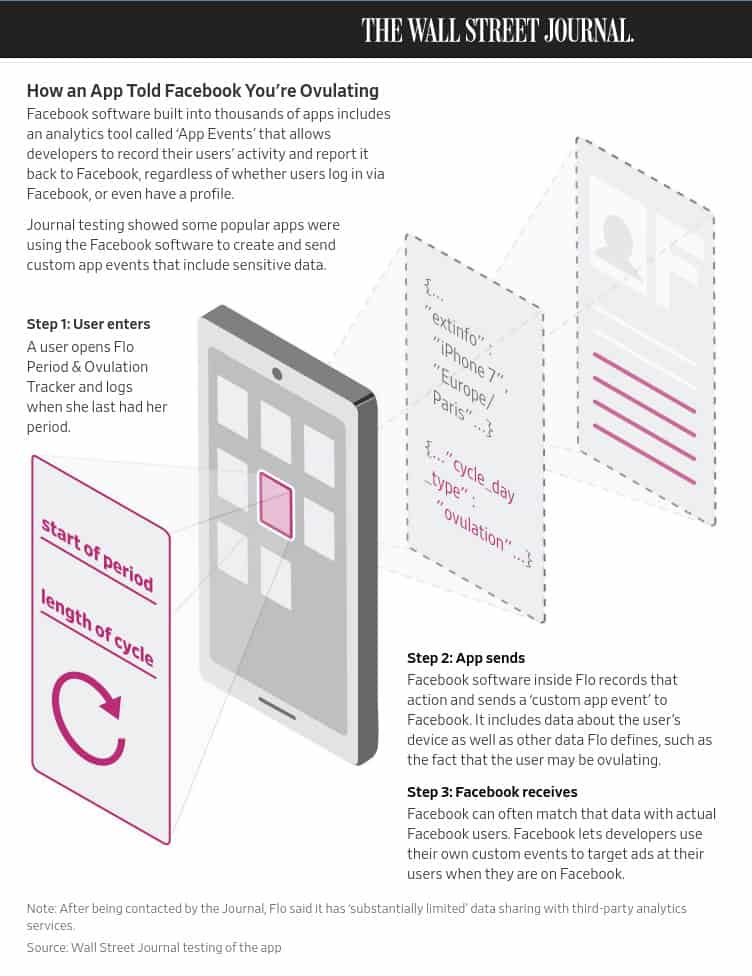
We’re not trying to accuse any of these companies of doing anything dishonest. Facebook says the companies were mistaken in sending such personal data to them and that everyone involved is taking steps to prevent such problems in the future.
What we are trying to do is show you how your personal data can find its way to places you would never expect it to go.
Apps Can Ignore Permissions and Still Grab Your Data
Okay. We’re still not accusing anyone of anything. But according to the nonprofit research center International Computer Science Institute, thousands of Android apps have the ability to take data from your phone even when you don’t give them permission to do so. So says this July 2019 report from Fox 2 News in Saint Louis.
Researchers at the Institute discovered 60 apps that were actively circumventing the permissions and a large number of apps that contain code that would allow them to do so.
One example dealt with permission to see the location of the phone. A user can turn off the Location permission, blocking that app from accessing that information directly.
However, photos taken on a phone contain metadata which includes the location where the photo was taken. Apparently, some photo apps relied on the metadata to find the location of the photo. In effect, the app ignored the intent of the user, which was not to share the location of the photo with the app.
The researchers who found the problem say that the activities might not be malicious or intentionally circumventing permissions. Indeed Google classified this problem as a bug and paid the researchers a bounty for finding the problem. A fix is supposed to be included in the upcoming Android Q update.
Things to Do to Minimize the Risk to Your Personal Data
Now that you’ve seen what can happen to your personal data when apps have access to it, here are some things you can do to protect yourself.
Wait Before Installing a New App
While it is exciting to be the first one in your group to use a new app, it is also risky. If you are a computer industry old-timer like this author, you may remember a rule of thumb that went something like this, “Never install a new program from XXXXXXXX (name hidden to protect the guilty) until they have released their third update.” That was way back in the early days of the personal computer, but it is still a good philosophy. Things just move a lot faster now.
If you wait 3 or 4 weeks to download a new app, you give other people the time to find any problems with the app. Not just any privacy violations, but bugs and other issues as well. There may even be an update or two (or more) that fixes any problems by the time you download the app.
Look for Reviews Before Installing a New App

If you wait a few weeks before installing a popular new app, you should be able to find some decent reviews. Sometimes there will be lots of word of mouth warnings about an app (see our story on FaceApp for a recent example), but that is the exception.
Most of the time, you will need to look for reviews to see if there are any issues with a particular app. You can get a sense of the situation by checking the reviews in the app store. But for the most insight into an app, you’ll want to wait a couple of weeks after launch and look for actual reviews using your favorite search engine.
Research the Publisher of the App
Even if you can’t find reviews of a particular app, you may be able to find information about the company that publishes it. Check out their website. See if their name comes up associated with terms like “scandal,” “hack,” or “scam.” If you don’t find any problems, it doesn’t guarantee that your data is not at risk, but finding lots of problems with a publisher is a good sign you should look for an app from someone else.
Consider Paying for Apps
This is more of a philosophical approach than a universal solution. If an app is free, it is likely that the developers are making money by selling whatever personal data the app has access to.
If you pay for an app, the developers have a way to make money that doesn’t involve stealing your personal data. This doesn’t guarantee an app won’t mine your data, and it doesn’t prevent third-party library developers from doing so. But in theory, they won’t have to.
Unless the app you are interested in does something totally unique, there are probably paid competitors available. If there are paid competitors, they are easy to find.
To find a competing paid app, simply:
- Think of a word or short phrase that describes what the app does. For this example, I am interested in a VPN app for my Android phone.
- Go to the app store or read our best vpn post
- Enter the word or phrase into the search box.
- The app store will return matching apps in a list.
- Take a look at any paid competitors, and compare the personal data they request to that requested by the free app. If the free app requests additional data, the paid app may be the better option.
Read the Fine Print
Finally, before installing an app, read the fine print. See what permissions the app wants you to give it. Do they make sense for this particular app? If not, they are probably mining and selling your data.

For an extreme example, I once was looking for flashlight apps. You know, the kind of app that turns on the phone’s camera flash and keeps it on so you can use the phone as a flashlight. One app looked promising until I looked at the Permissions it requested. It wanted crazy stuff like location data and full network access.
Since the app only turned the light on and off, I couldn’t see a legitimate reason for it to have these additional permissions. I chose to install a different app that didn’t ask for personal data unrelated to the problem at hand.
Also avoid apps in areas like casino, free vpns, torrenting etc as they are always full of weird stuff.
Conclusion: Many Smartphone Apps ARE Mining Your Personal Data
Let’s wrap this up. Many smartphone apps are stealing your personal data and doing all sorts of stuff with it. There are steps you can take to reduce the risk of an app using your data in ways you don’t like. But with the constant change in the smartphone world, and unscrupulous advertisers, programmers, and hackers eyeing all that delicious data on your phone, you can never be 100% sure your data is safe.

Besides taking the protective steps we’ve listed here, it may be time to think about exactly what data you store on your phone. Having everything at your fingertips (or in your pocket) is a great convenience, but the more apps you run, the bigger the target you are.
Do you really need access to your bank account from your phone? To record your ovulation status there? To carry those pictures of your significant other wherever you go? Do you really need to take your phone with you if you are going to a political rally or a medical clinic or some other sensitive location?
Like you, we love our smartphones. But we all need a little time away from those we love. Maybe it is time to apply that philosophy to our phones too.
References
- What is Data Mining?
- AnandTech’s review on Samsung Galaxy S9
- What is Data Anonymization?

![A Beginner’s Guide to Monero – What Is XMR? [Updated 2023]](https://cd.blokt.com/wp-content/uploads/2019/04/Beginners-guide-to-Monero-2-218x150.png)

![Best 5 Bitcoin Sports Betting Sites [2023] (Analyzed & Approved) Best Bitcoin Betting Sites](https://cd.blokt.com/wp-content/uploads/2020/05/best-bitcoin-betting-sites-218x150.png)

